4) IAM Policies Hands On- AWS Certified Solutions Architect Associate Course SAA-C02- Okay so let’s play with IAM policies. So if we go into my user groups right now
NOTE– In the below pictures on the left hand side I logged into my Root User Account and opened IAM, on the right hand side I opened IAM User Account.
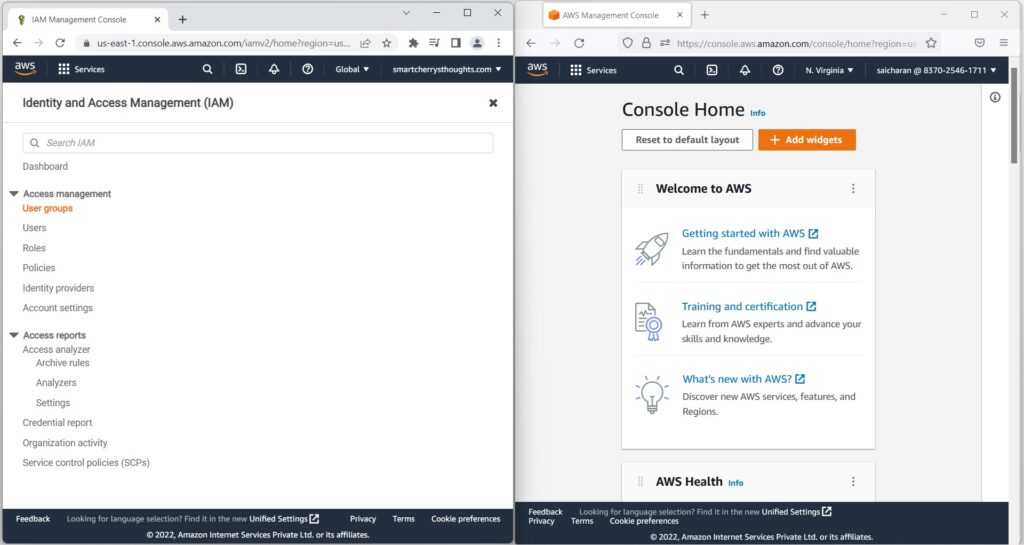
- I can see that my group admin contains one user saicharan(click on admin)
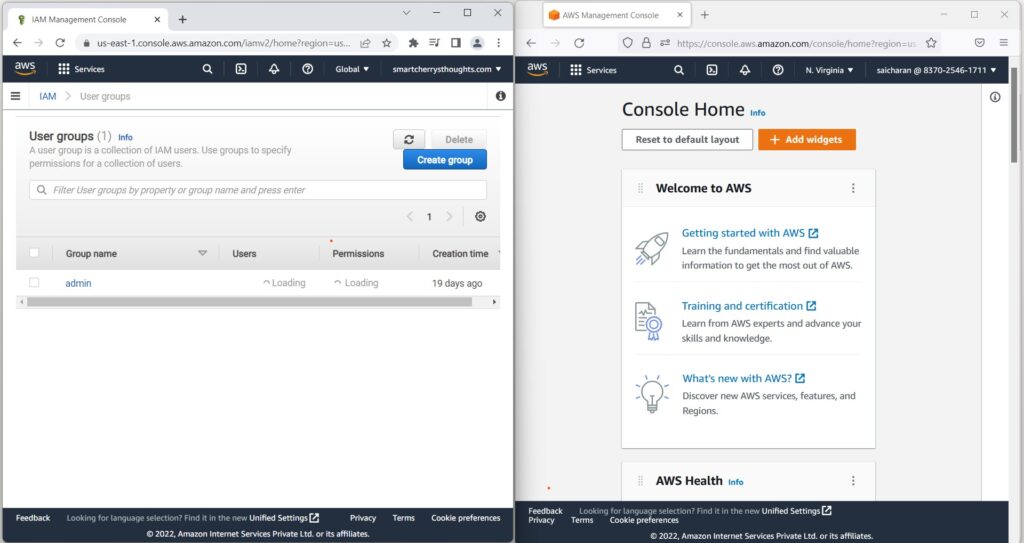
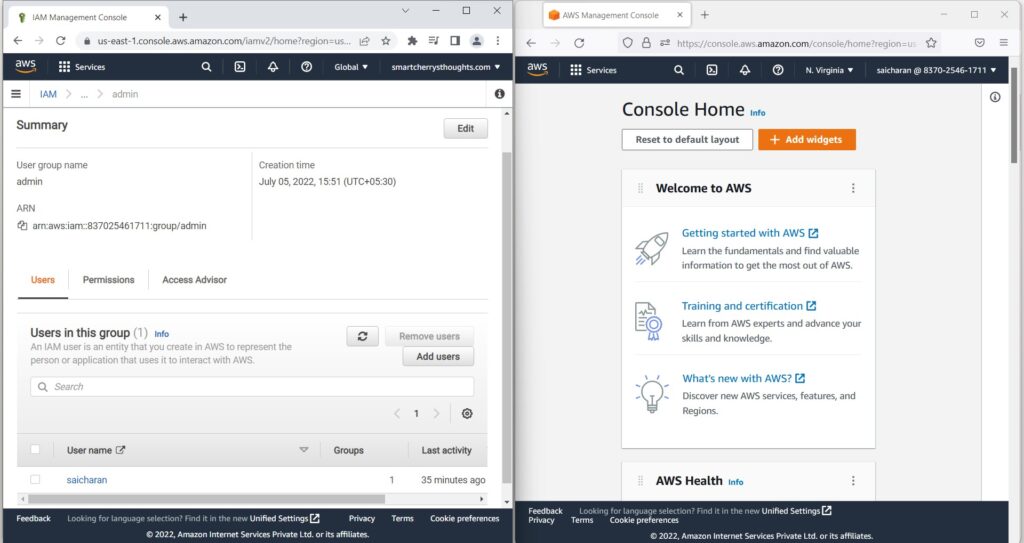
- So if I go on the right hand side and go to my Services
- and I go to IAM, so I’ll go to the IAM service, see below picture
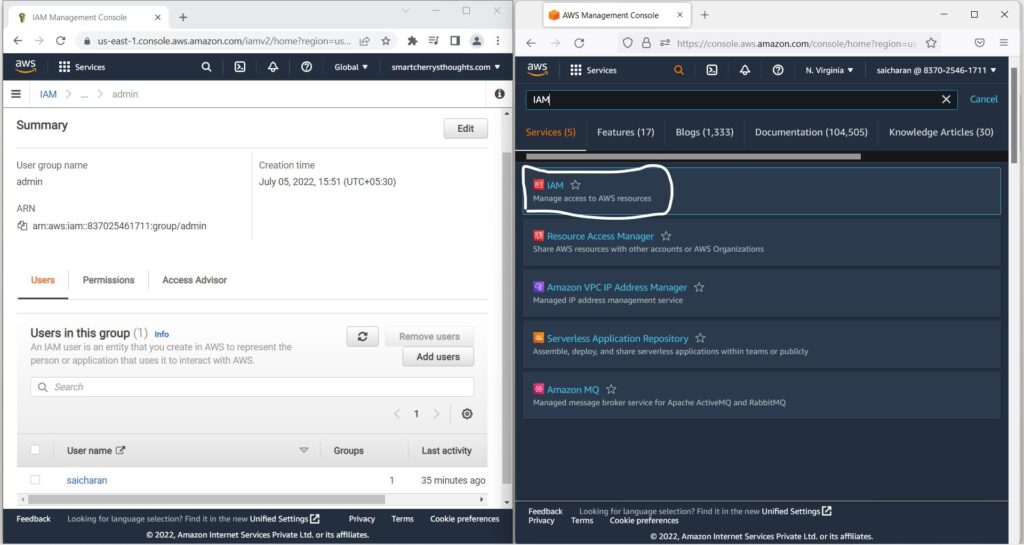
- I will show you one thing.
- So, this user is an IAM user.
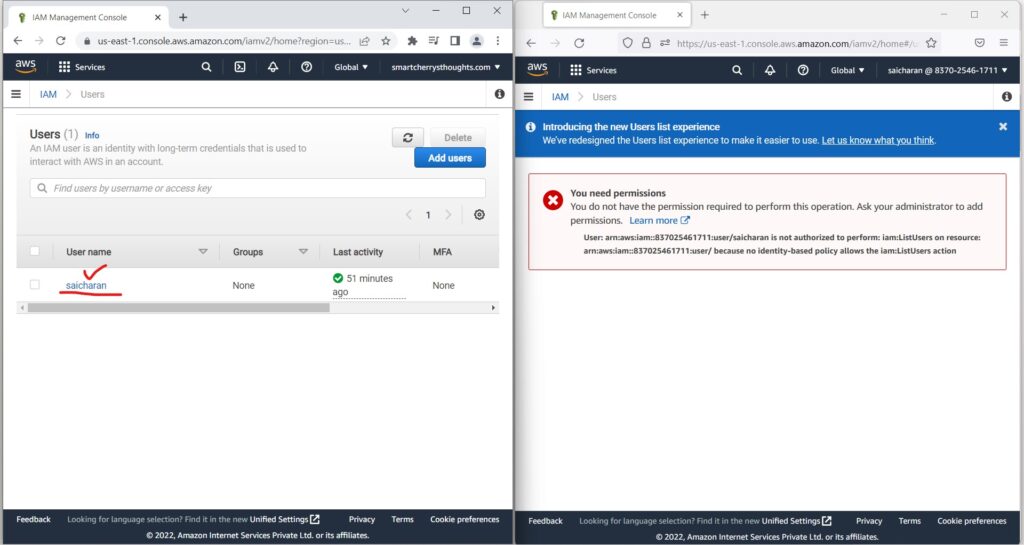
- And therefore, if you go to, for example, users
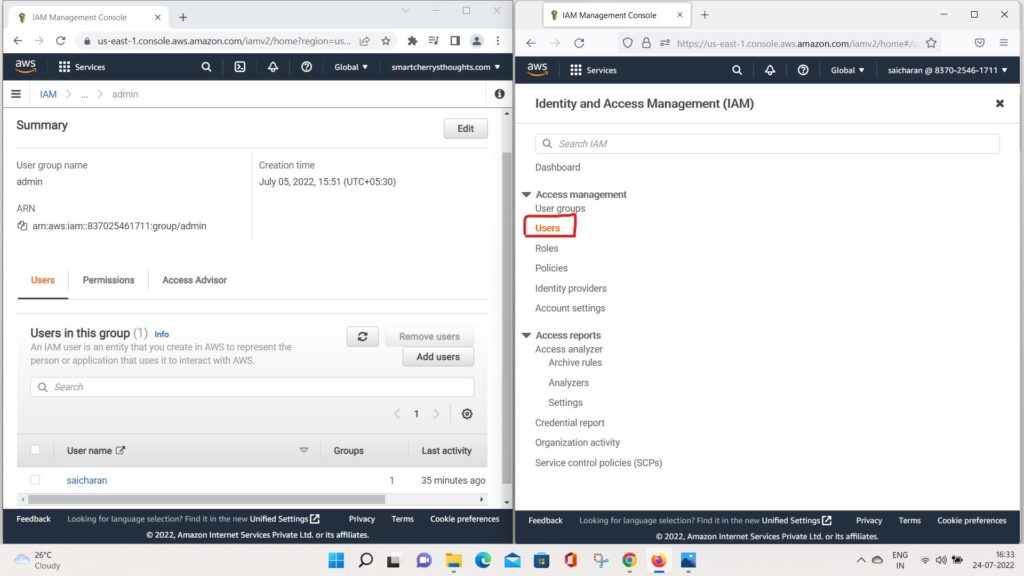
- you can see all the users
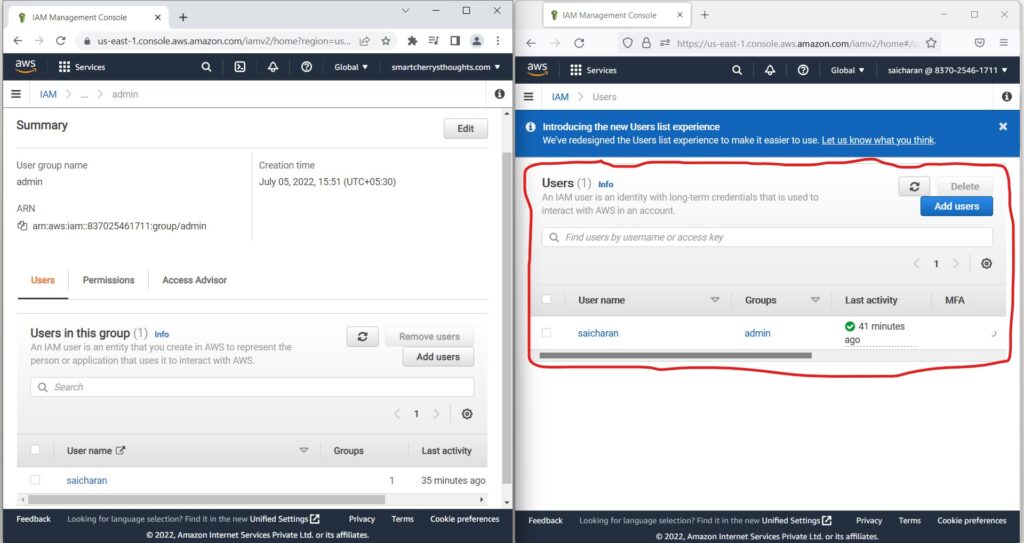
- Okay, great.
- So now what I’m going to do is I’m going to Remove saicharan from the admin group which is in root user account on left side
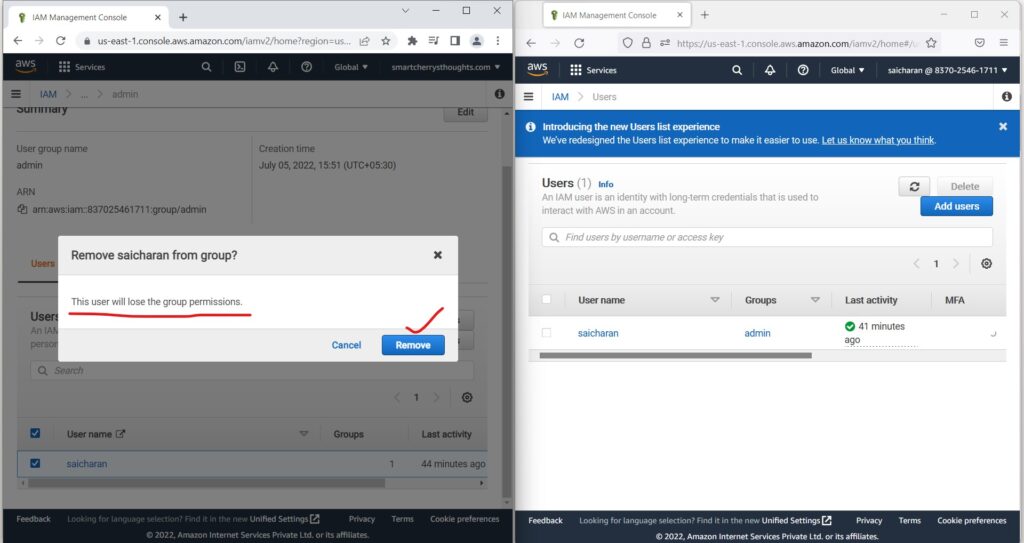
- I’m going to remove this user.
- and the user will lose the group permissions, that’s true.
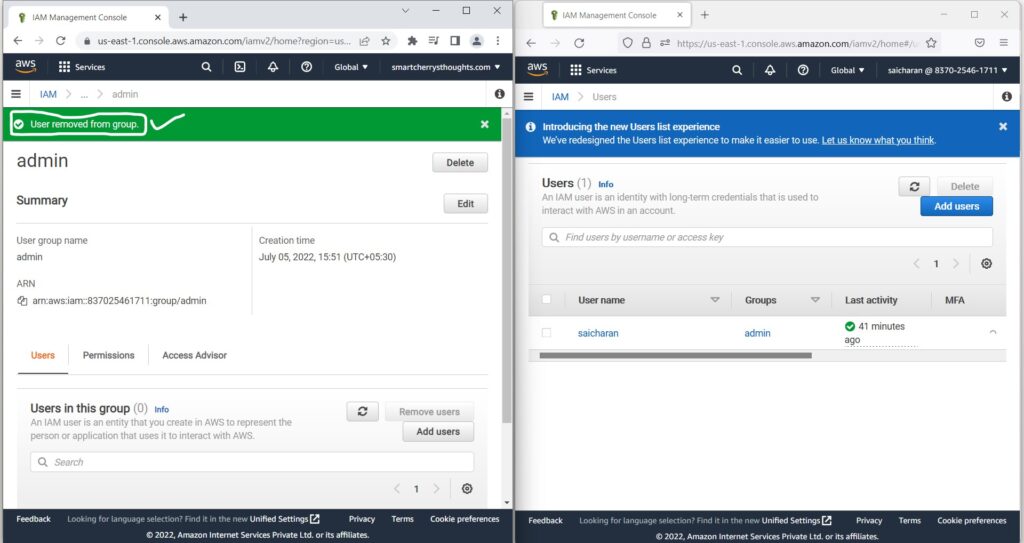
- So the user has been removed from the group.
- and how do we make sure that this is applied?
- Well, if i go on the right-hand side(admin user management console)
- and now refresh this page, as you can see,
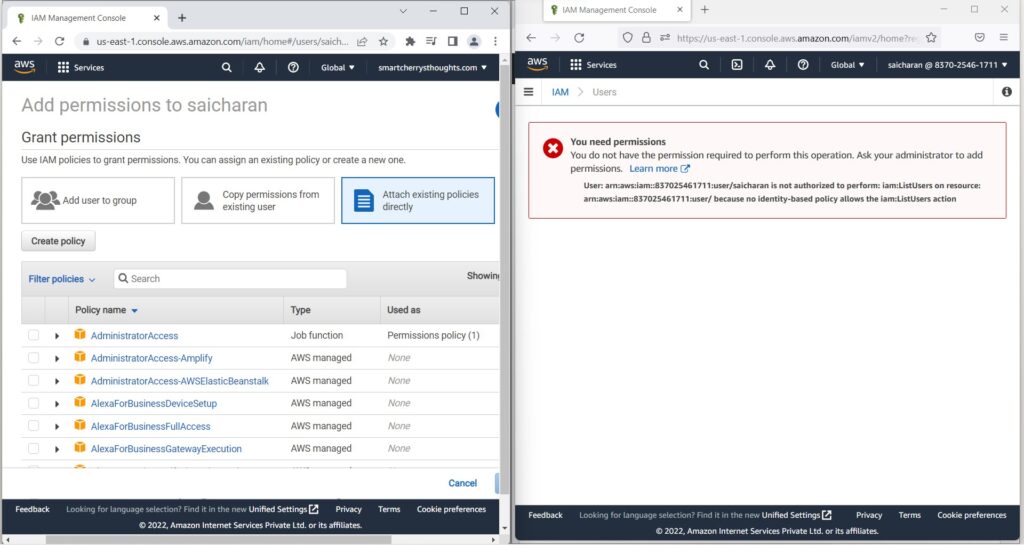
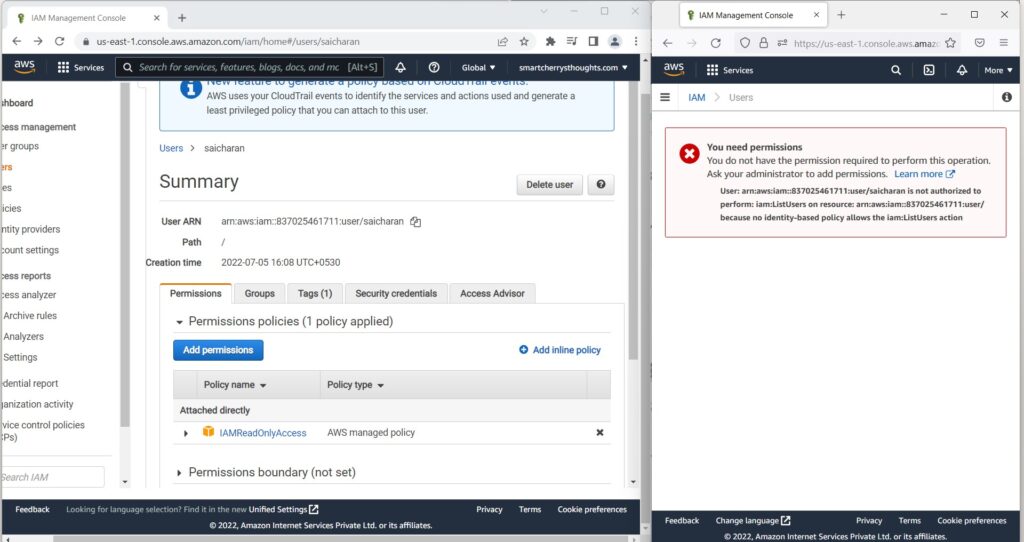
- I need permissions to access this page
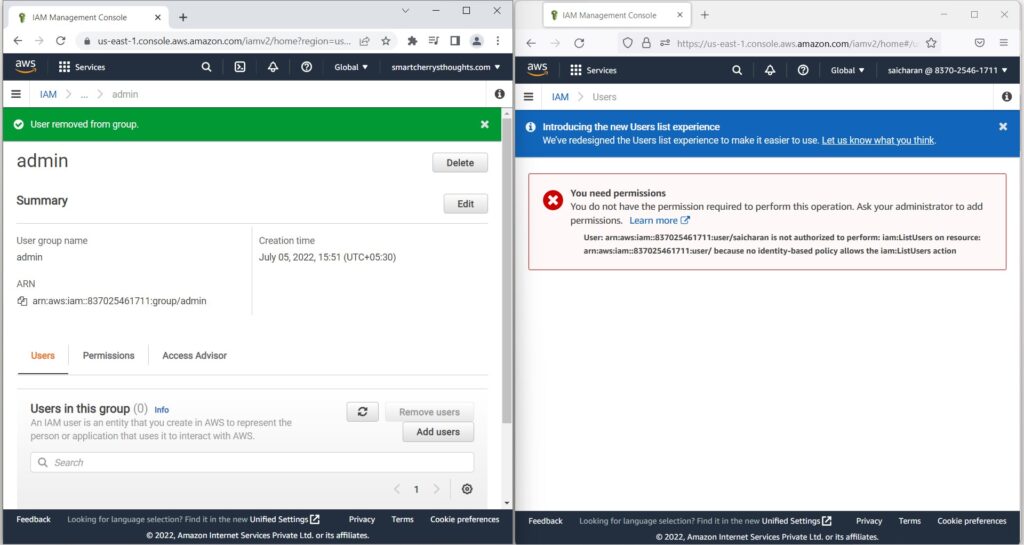
- and my user saicharan is not authorized
- to perform IamlistUsers on this page.
- user has been removed from the admin group and does not belong to group, user lost the group permission(policy that applied).
- So that makes sense right?
- Because we removed the user saicharan from the admin group.
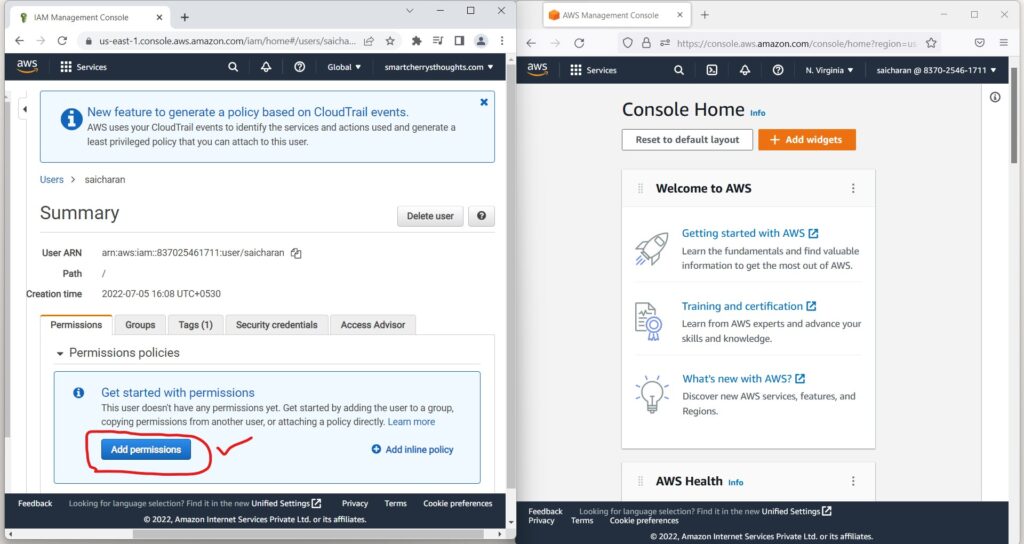
- So what i can do is i can fix this.
- and to fix it, i can go into my users.
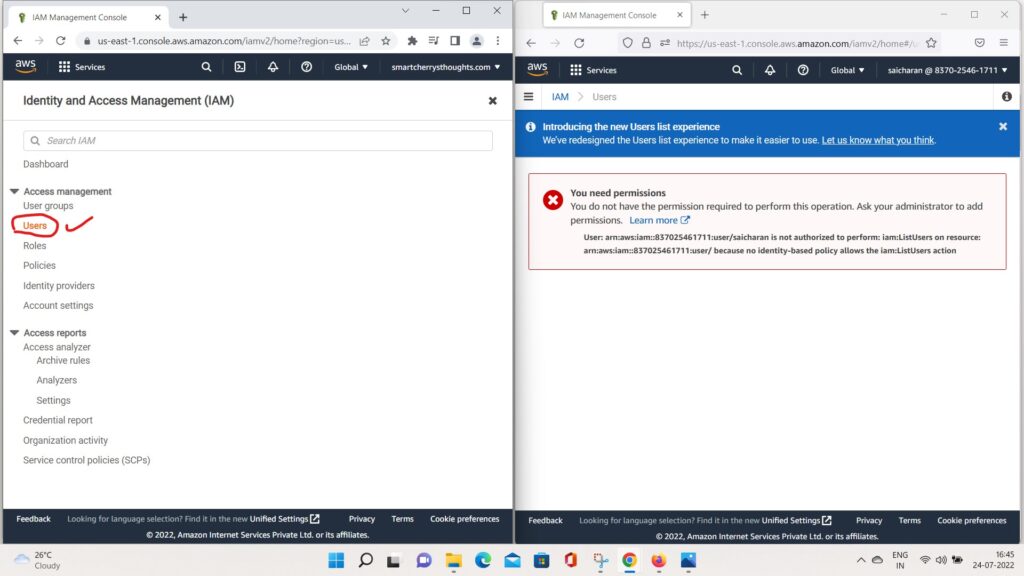
- go to saicharan
- and now I can attach permissions directly to my saicharan user.
- So two ways of doing so, number one is to add permissions
- and use policies that already exists or that you created.
- or add an inline policy to just add policies.
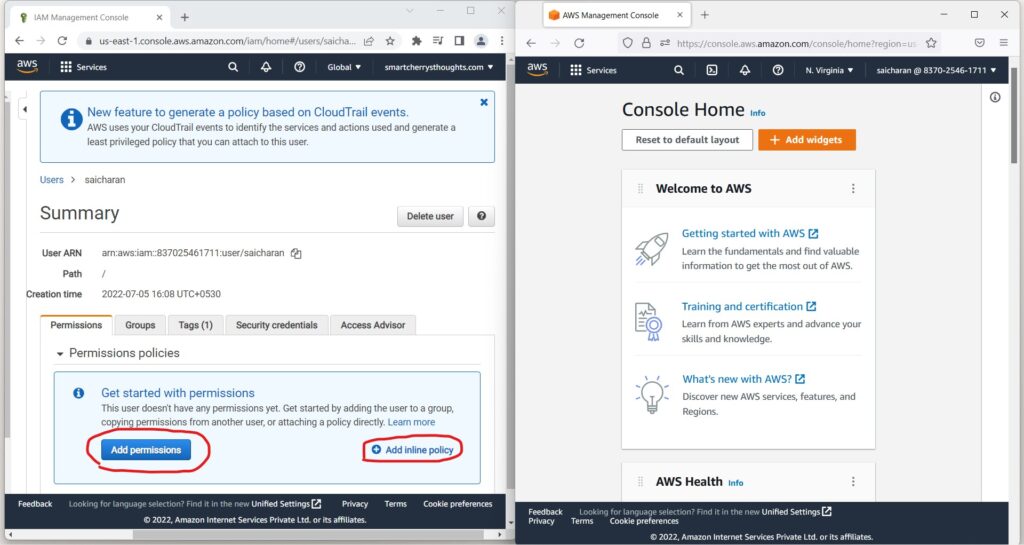
- So, I’m going to add permissions
- and I’m going to attach existing policies directly
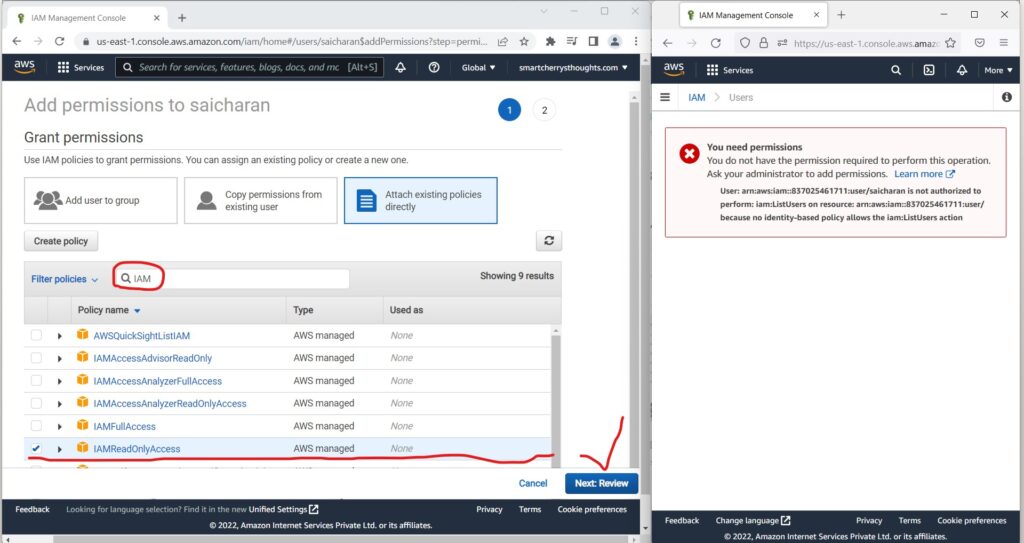
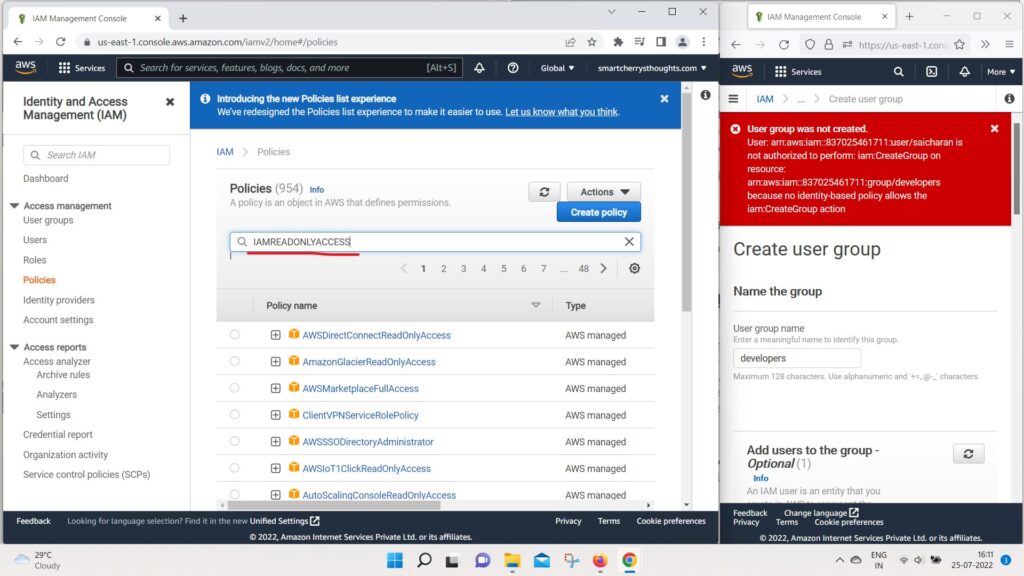
- and i will search for IAM
- And I’m going to look for IAM read-only access
- I review
- I add these permissions.
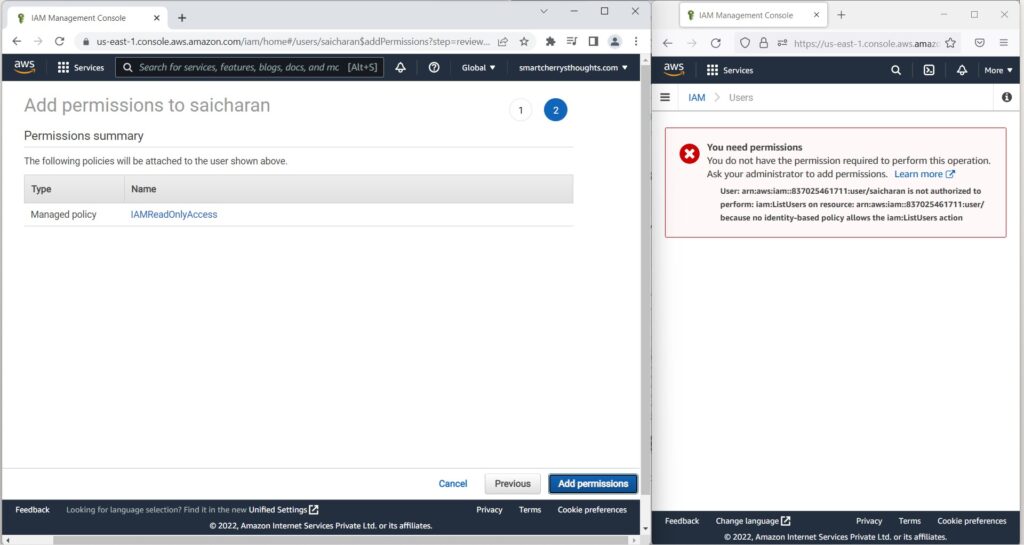
- and now my user saicharan has IAM read only access.
- What dies that mean?
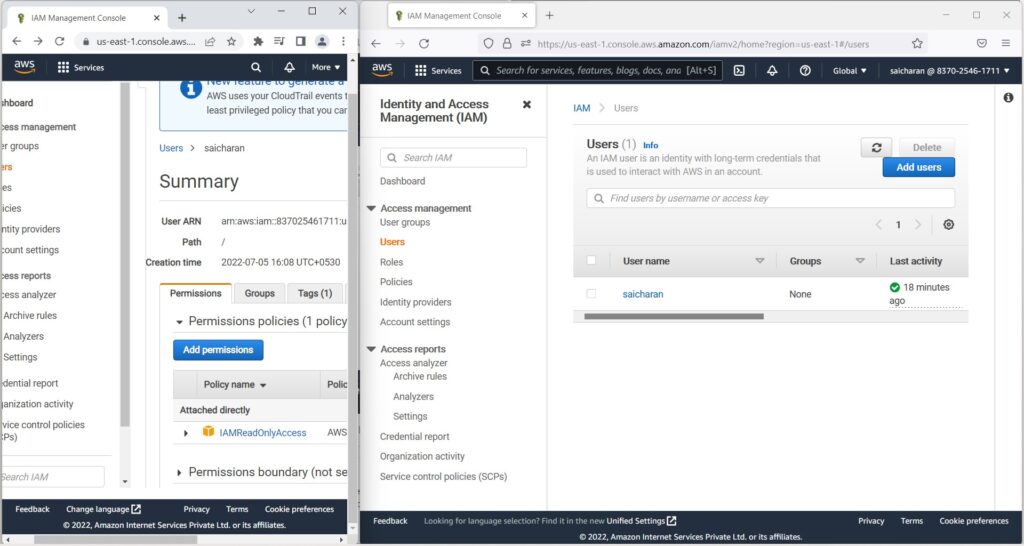
- That means that, for example, if I refresh this right side page…
- Then, as we can see, the user saicharan does exist.
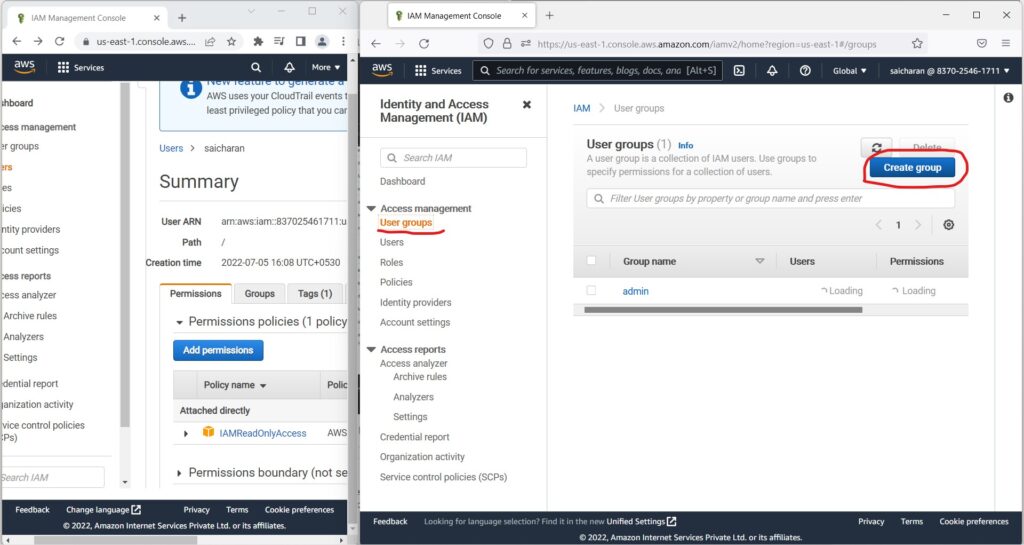
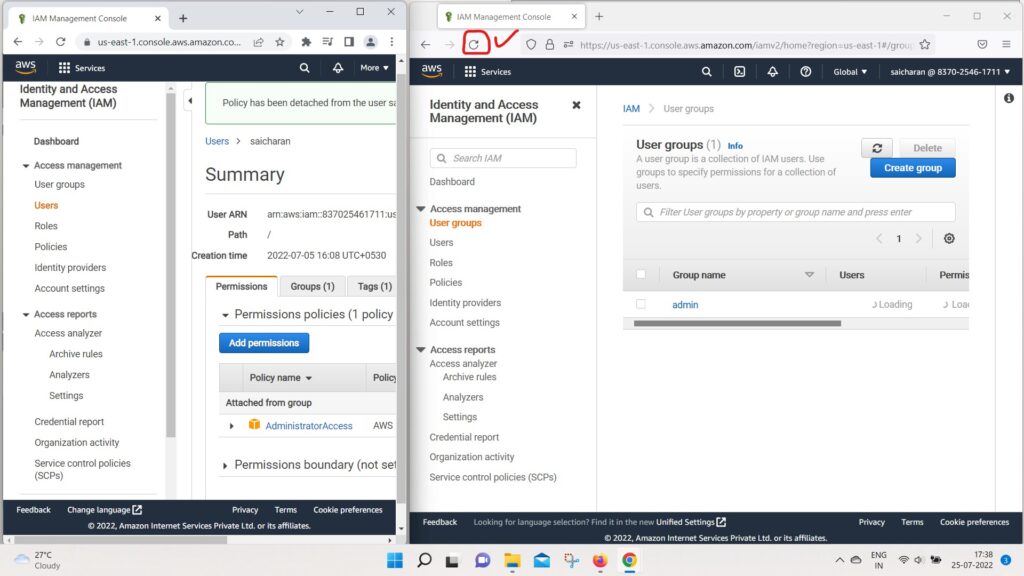
- But for example, if I go to User groups(right side window which is IAM user Account)
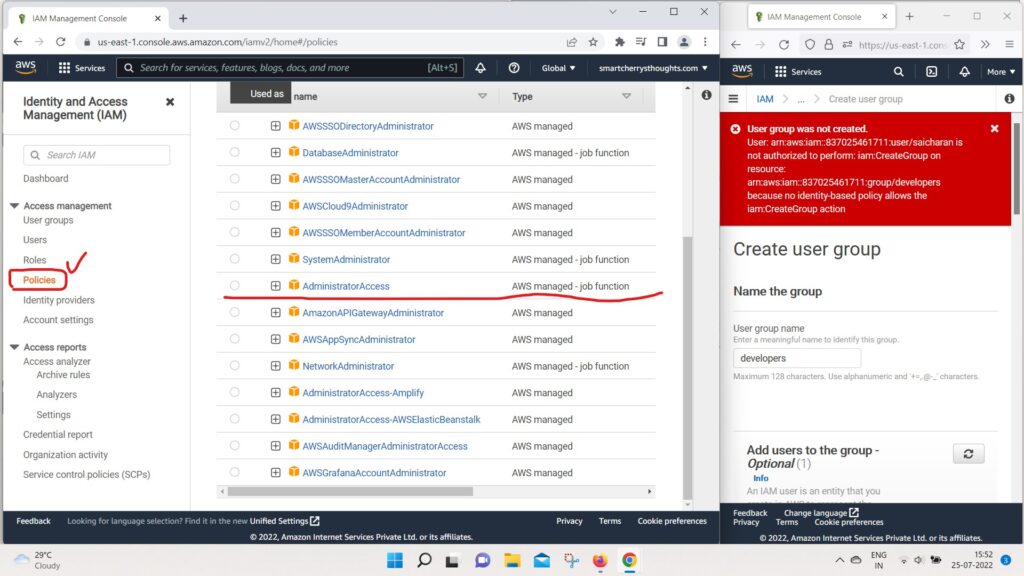
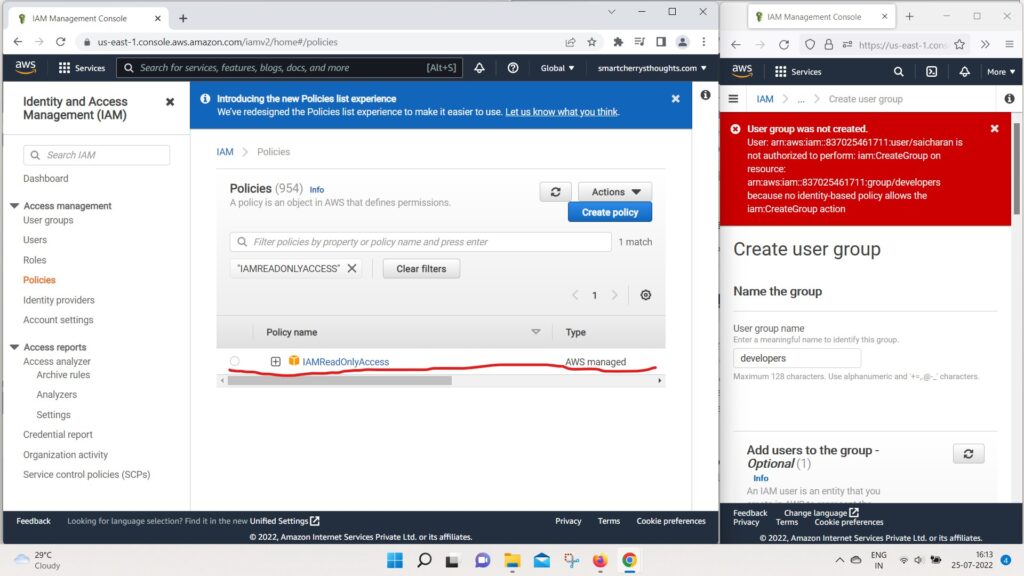
- and I try to create a group and call it “developers“
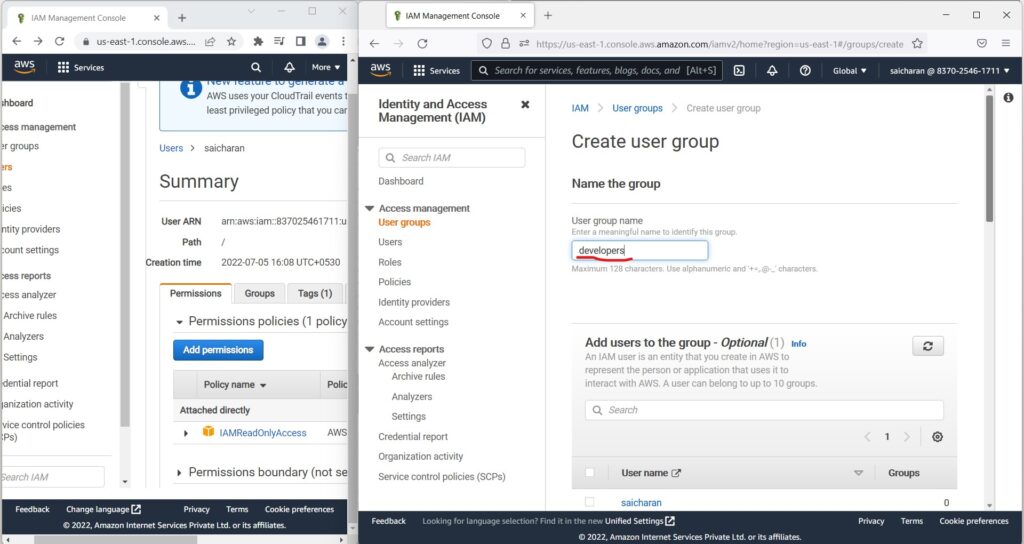
- and create this group.
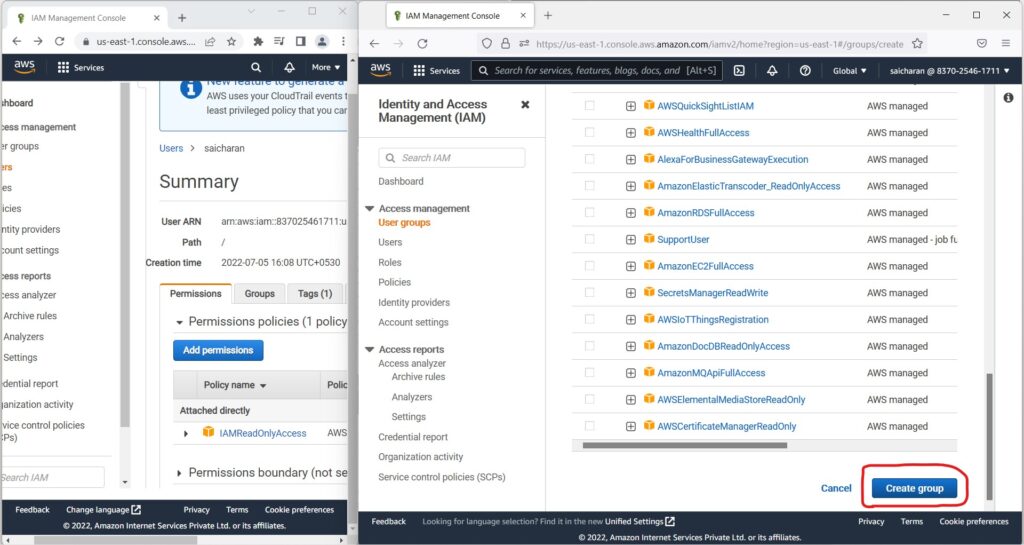
- I’m going to get an exception.
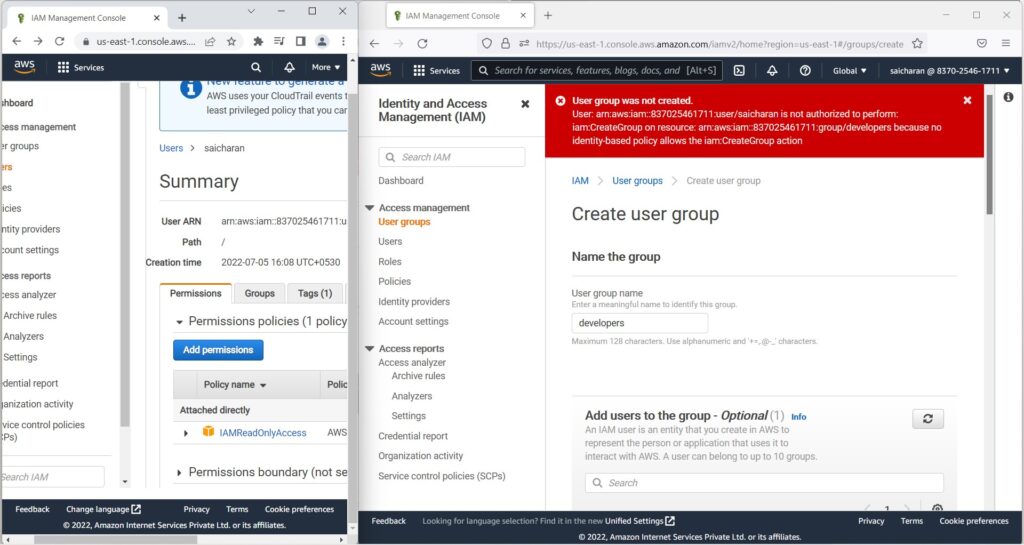
- because I’m not authorized to do create group,
- I was only authorized to have read-only access to IAM.
- So this really shows the power of IAM and so on.
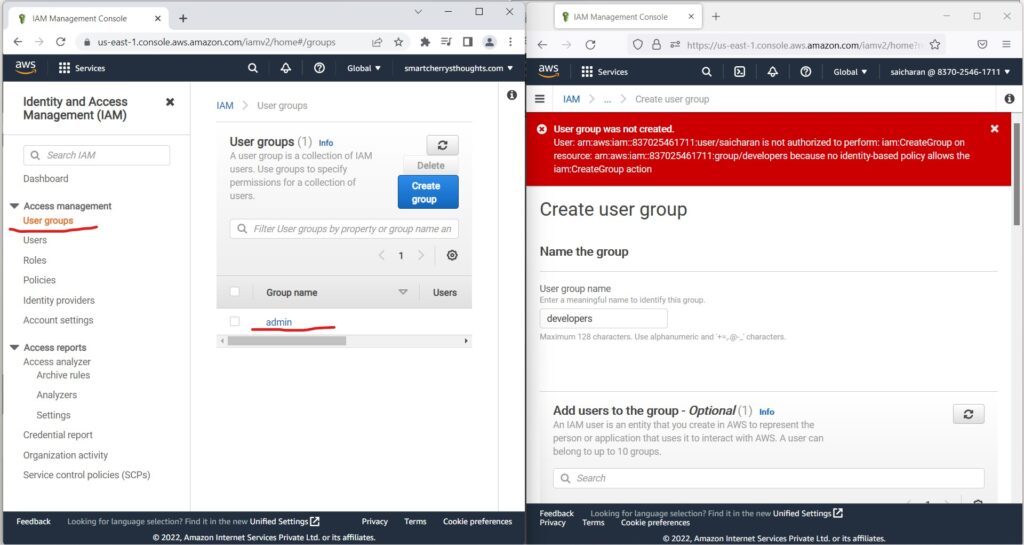
- So, now if I go to my user groups,(left hand side window, root user account), I Can do two things.
- So number one, I can go into the admin group
- and I’m going to add back
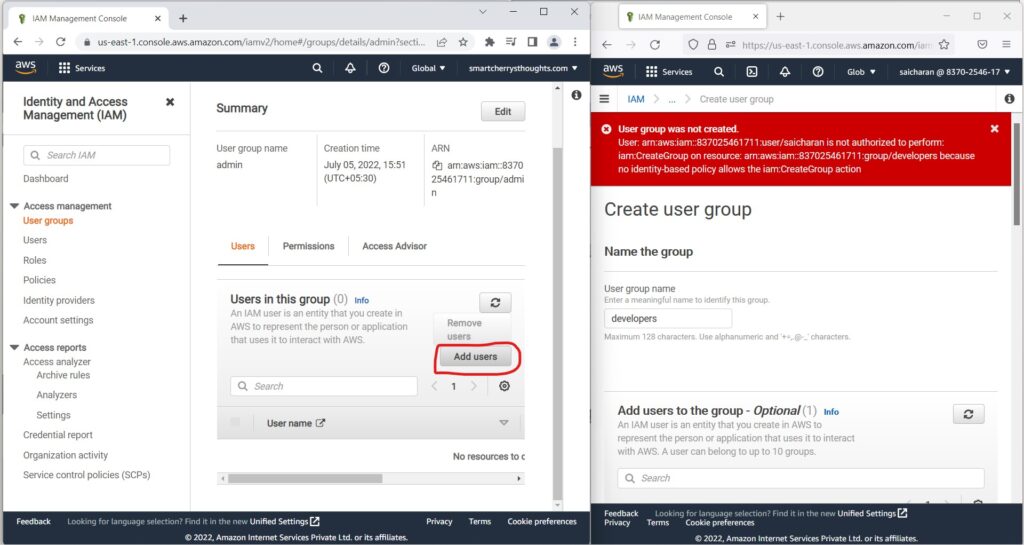
- this saicharan user so that we have administrator access
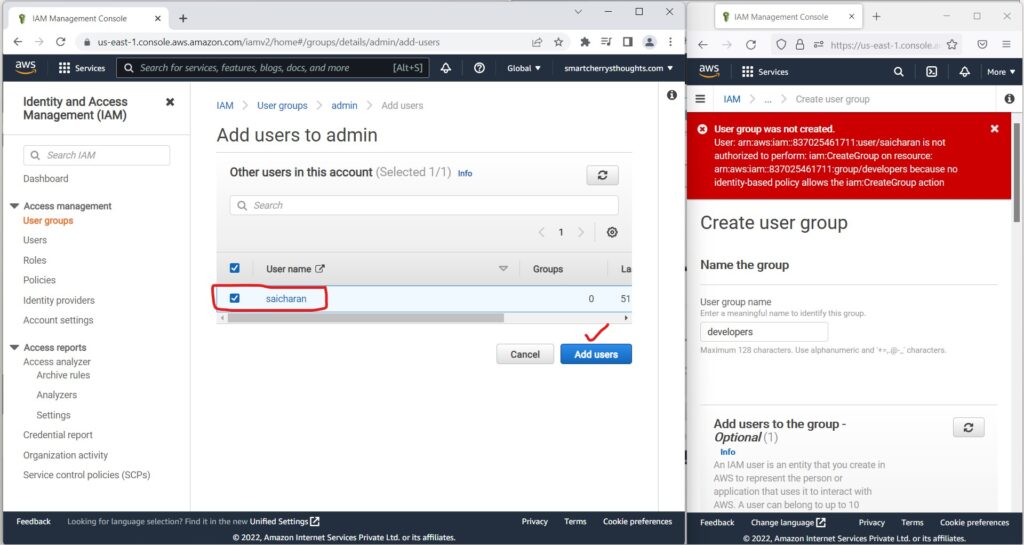
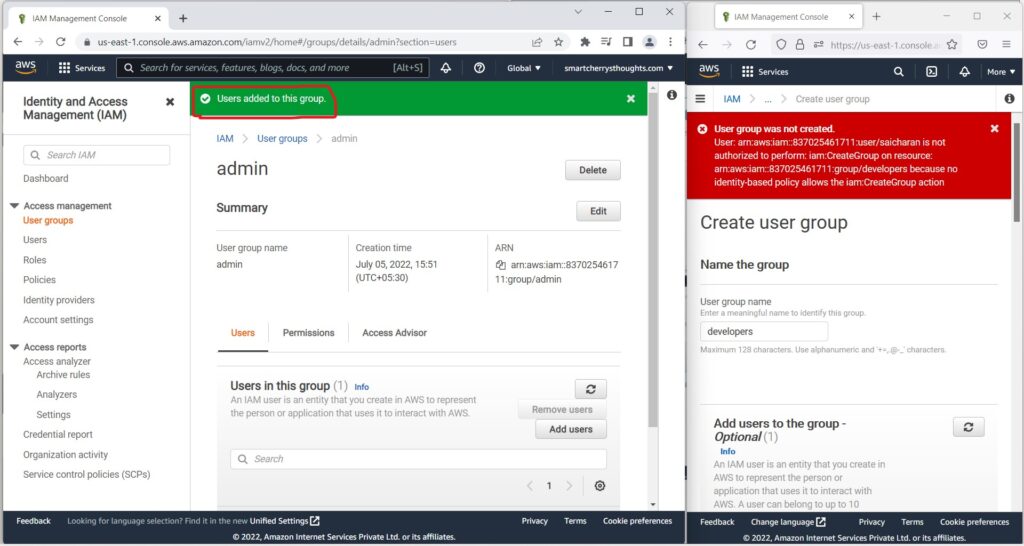
- The second thing I’m going to do is I’m going to
- create a group named “developers” (on left hand side window, this is root user account)
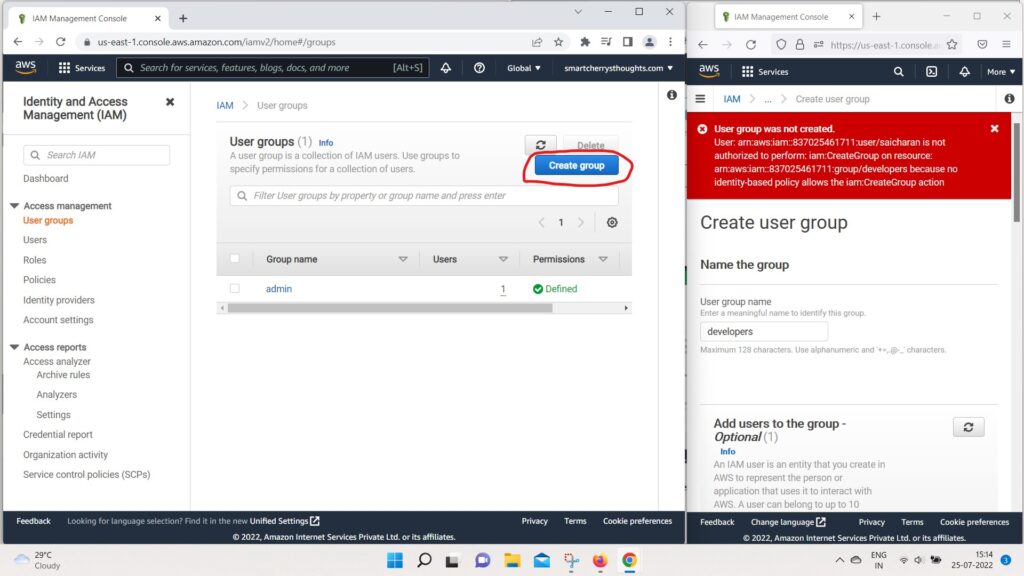
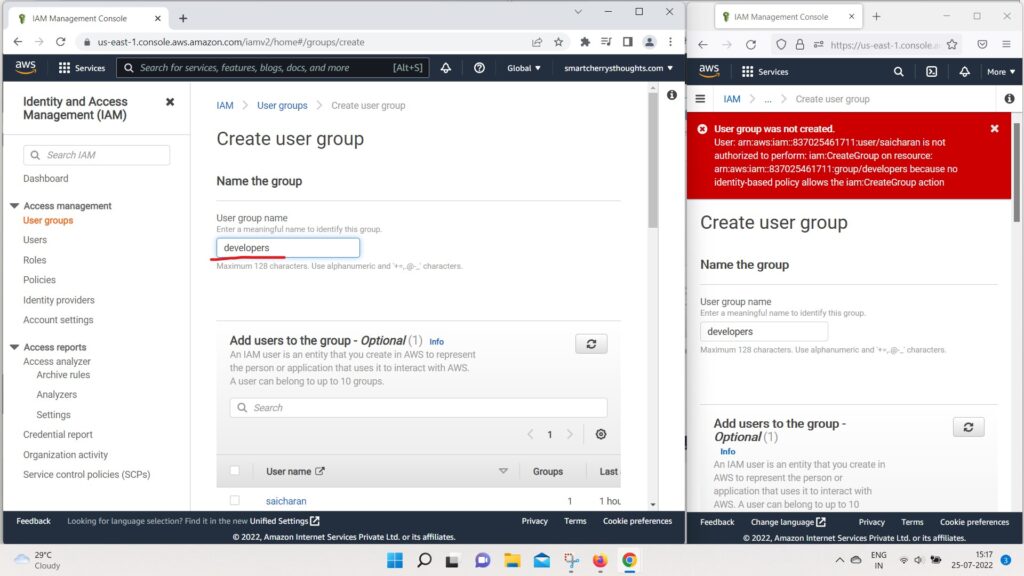
- And I’m also going to add saicharan into this group
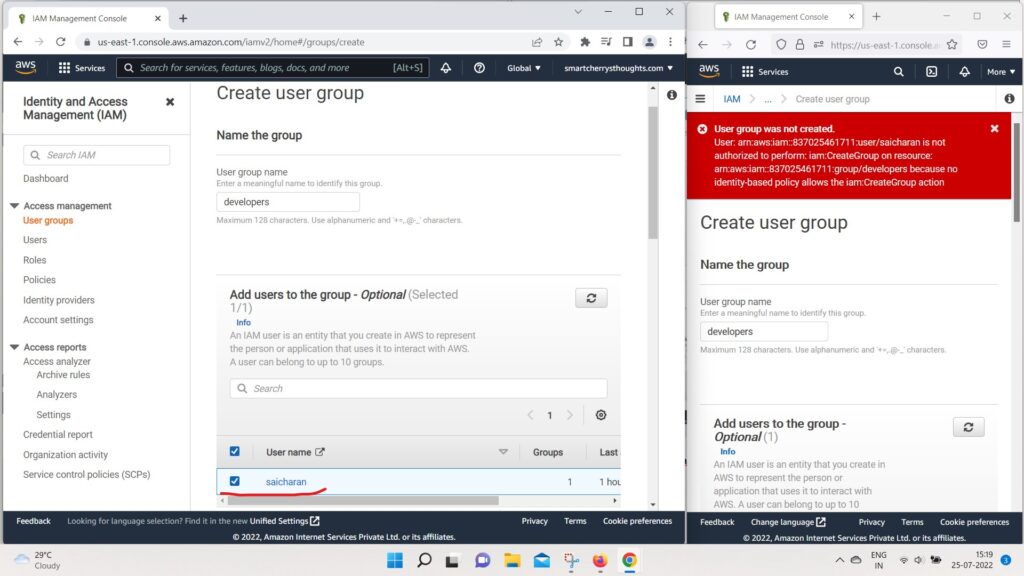
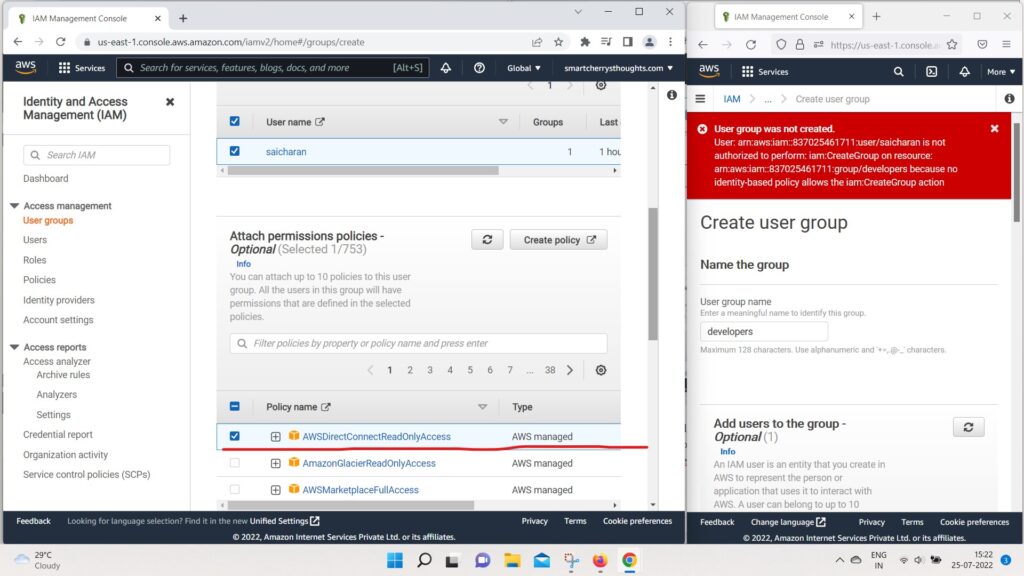
- and I’m going to attach a policy,
- whatever the first policy I Found
- it was AWSDirectConnectReadOnlyAccess
- and then create this group.
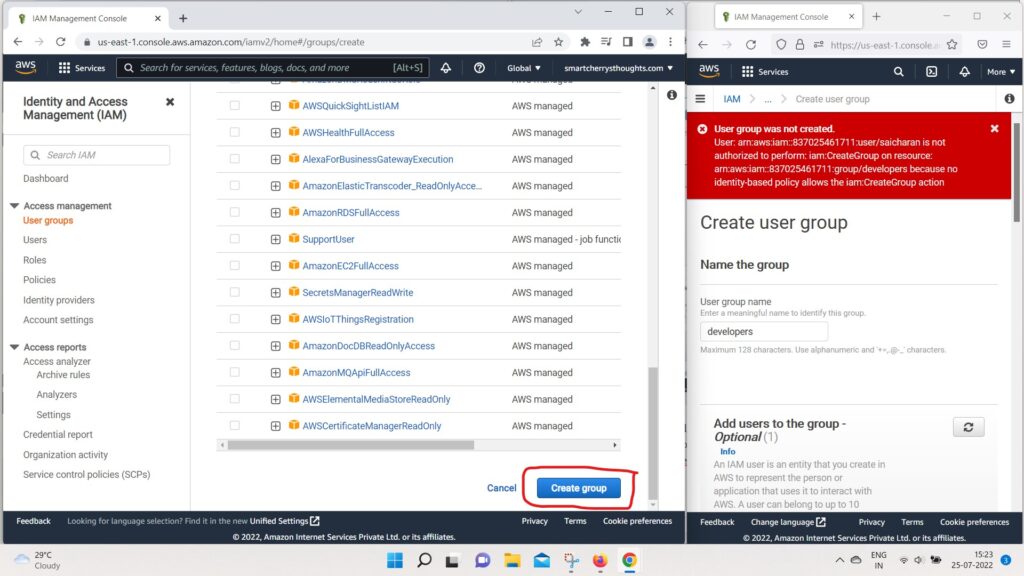
- It doesn’t matter which policy you’re attached to,
- I just want to show you a behavior.
- Okay so, now we have two groups,
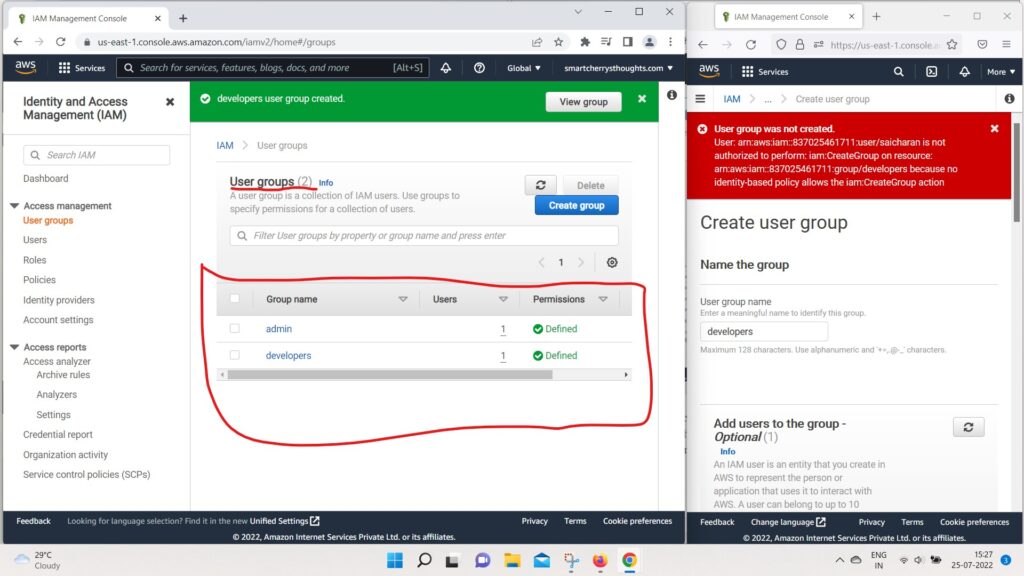
- we have admin and the developer group,
- and the user saicharan is in both groups.
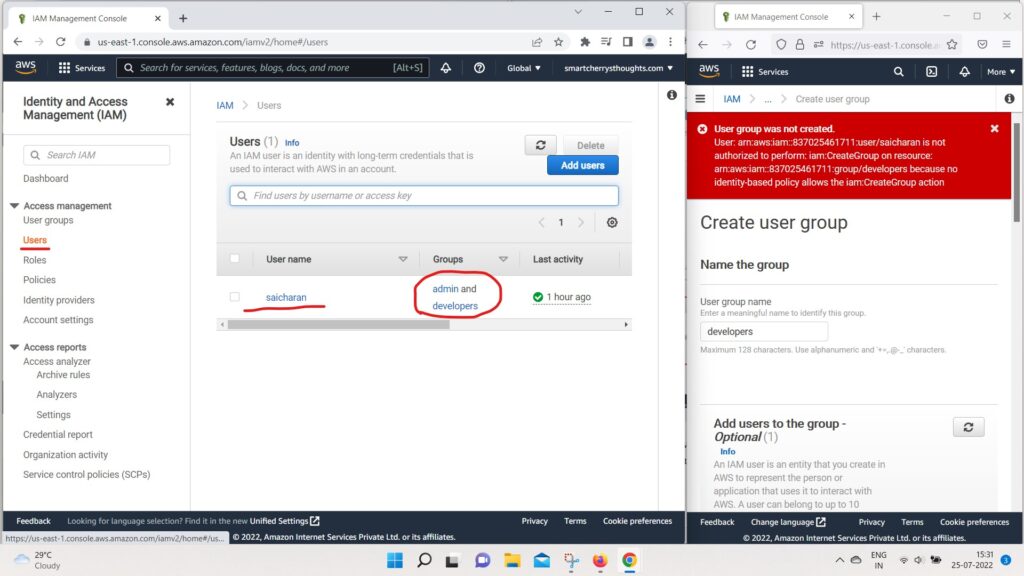
- So what’s going to happen is
- that if I click on the user saicharan
- and look at the policies it has, it has three policies
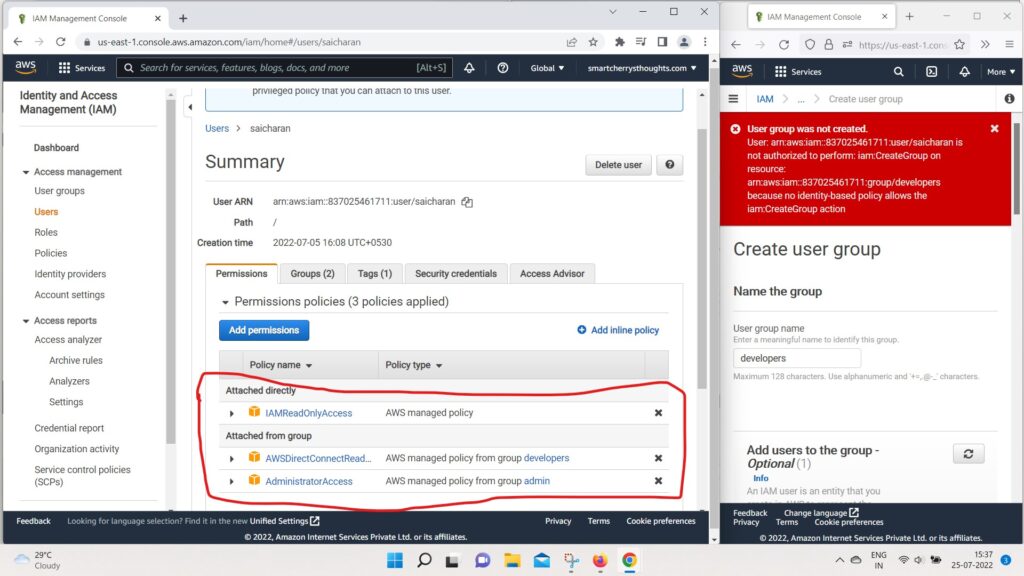
- One that was attached directly named IAM ReadOnlyAccess.
- One that was in two that were in Attached from groups.
- The first one is AWSdirectconnectreadonlyaccess from the group developers.
- and second one is, it was AdministratorAccess from the group admin.
- So, as we can see, the policies get inherited.
- in different ways through the IAM permissions.
- So finally, I want to show you how policies work.
- So if you go to policies.
- we have a list of all the policies available.
- within AWS right here, their managed policy.
- So this one is administrator access.
- and we’ve been using it before.
- Click on AdministratorAccess
- And if you look at the policy, JSON forum, as we can see
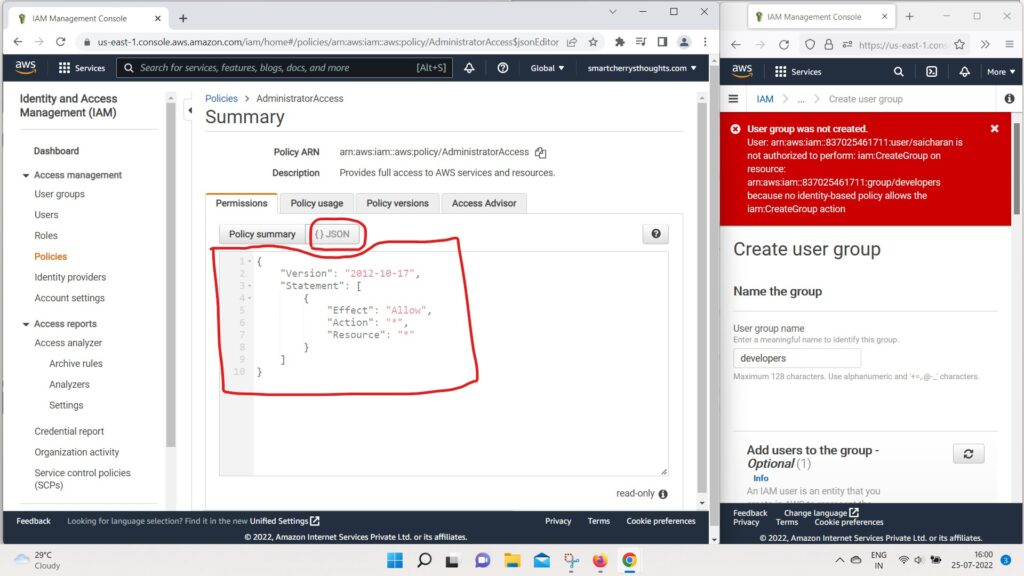
- we have a version and we have a statement
- that statement contains one statements
- and the Effect is Allow.
- So to authorize action is “*”
- that means any action resource is “*”,
- that means any resource.
- So we allow all the actions on all the resources.
- therefor making this policy an administrator access policy.
- we can go into policy summary as well.
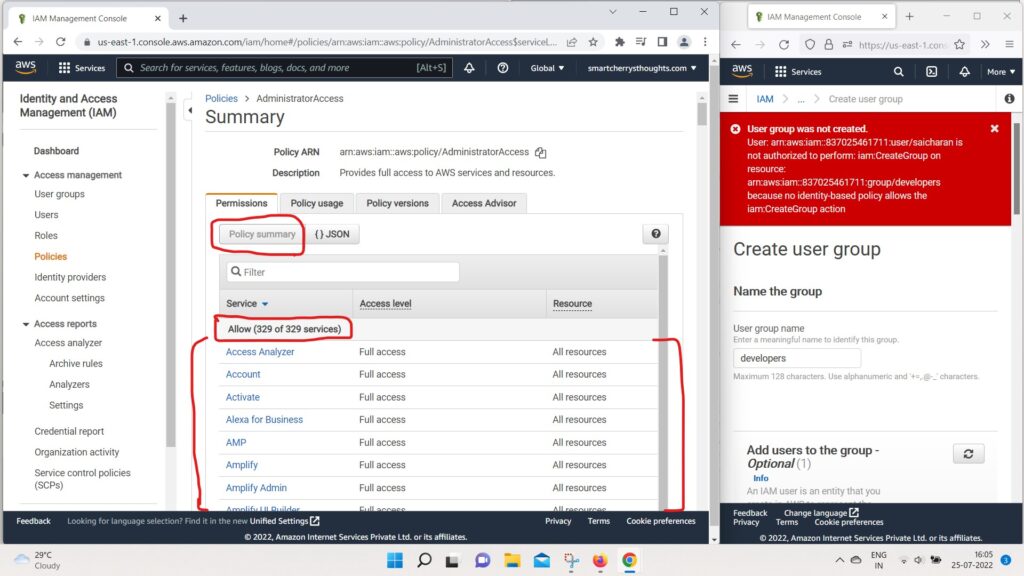
- and this is another view of the policy.
- we have allow on 329 services of 329.
- Now services get added all the time,
- so if you dont have the same number,
- dont worry, this course is up to date.
- So we can have a look at another policy.
- For example, the IAM read only policy
- that we’ve dealt with from before.
- So, this time allows one service out of 329
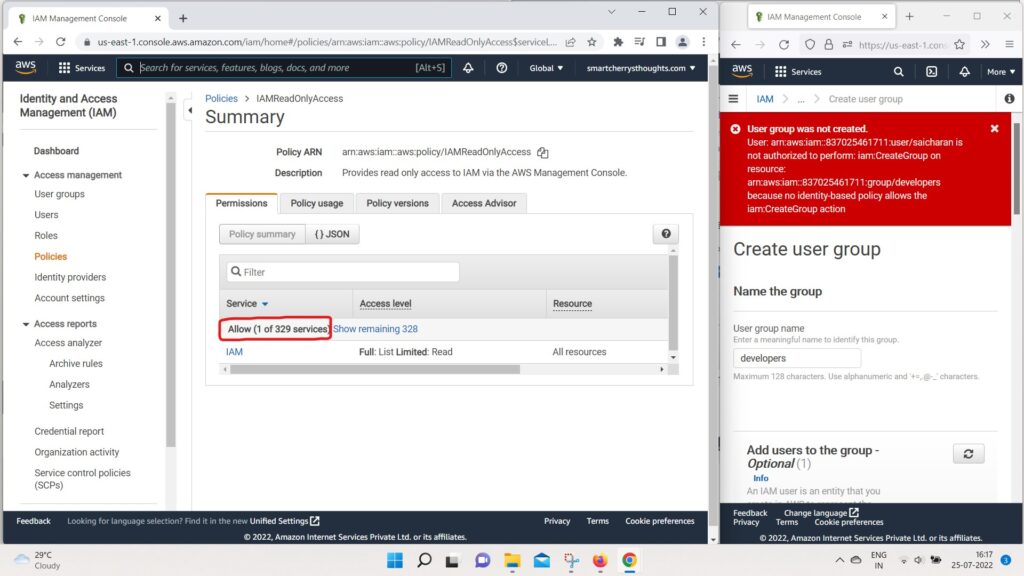
- which is IAM.
- And if we look at the JSON Documents,
- we can see all the actions that are authorized by this IAM read only access.
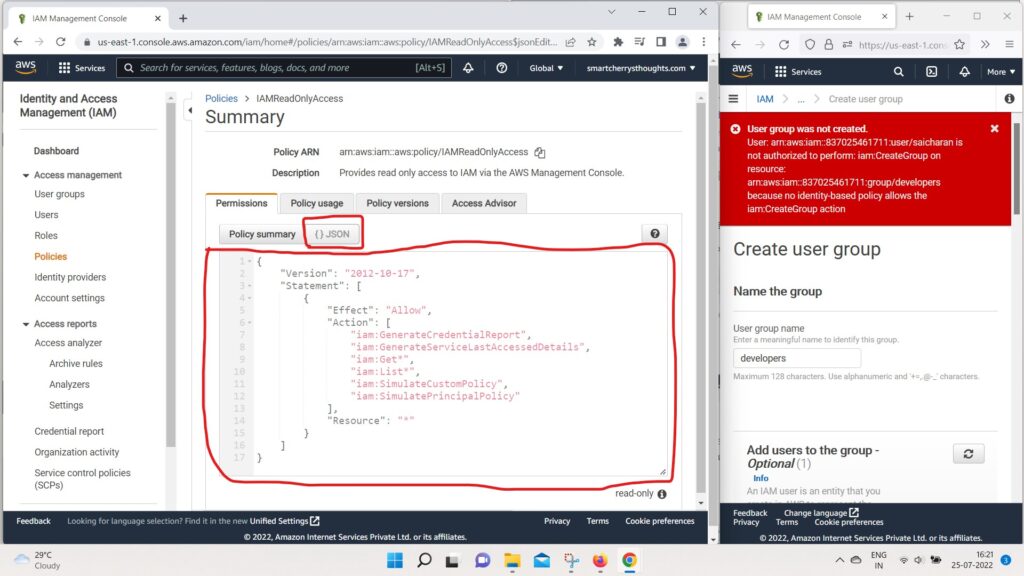
- So we get, for example, “iam:Get* ,
- the star GenerateCredentionalsReport,
- and so on, on the resource star
- There is also a way for you to create your own policy.
- So you can go back to your policies and create a policy
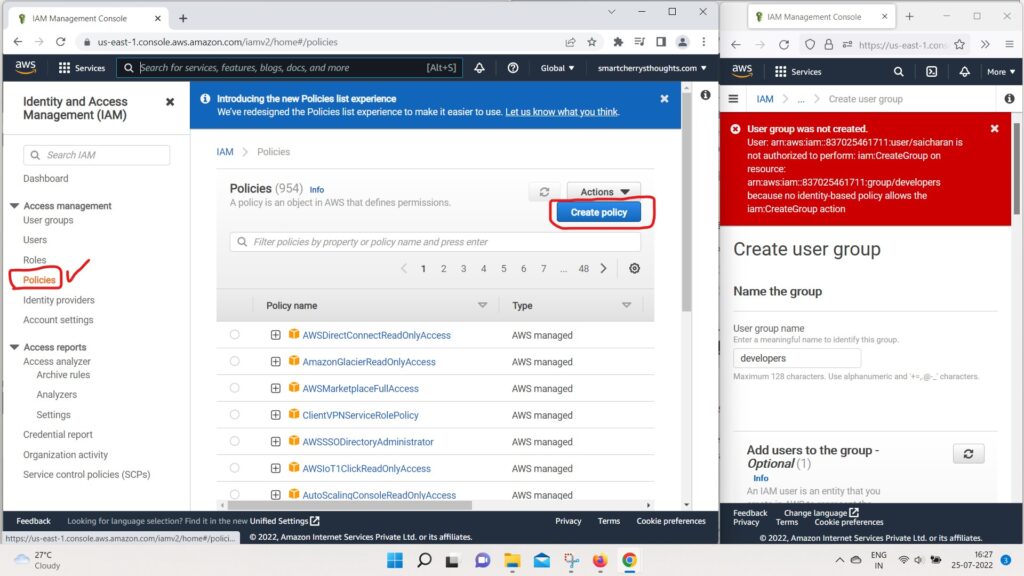
- and you have two ways of doing it.
- Either, you want to write plain and simple JSON
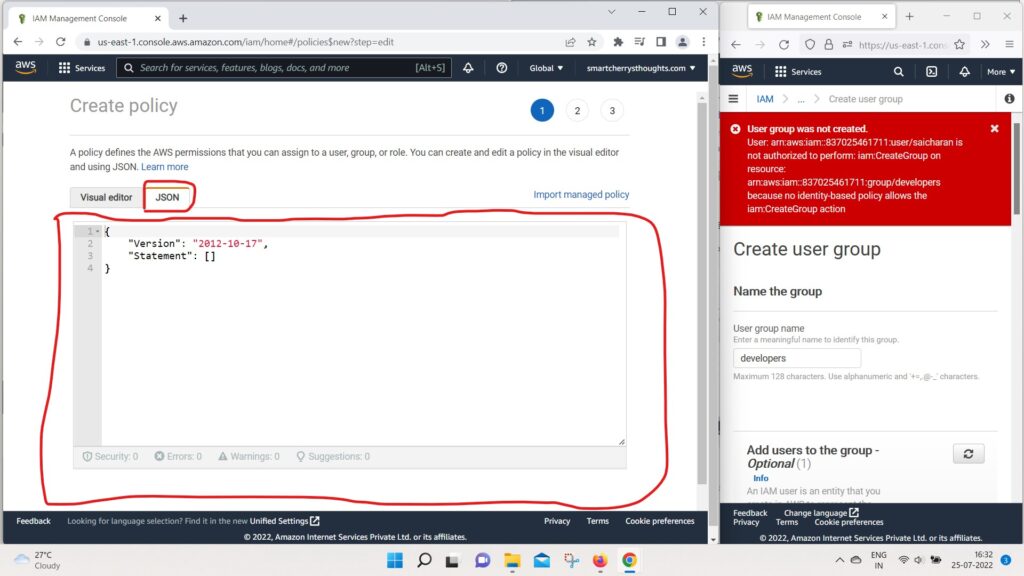
- or you can use the visual editor, and this is quite handy.
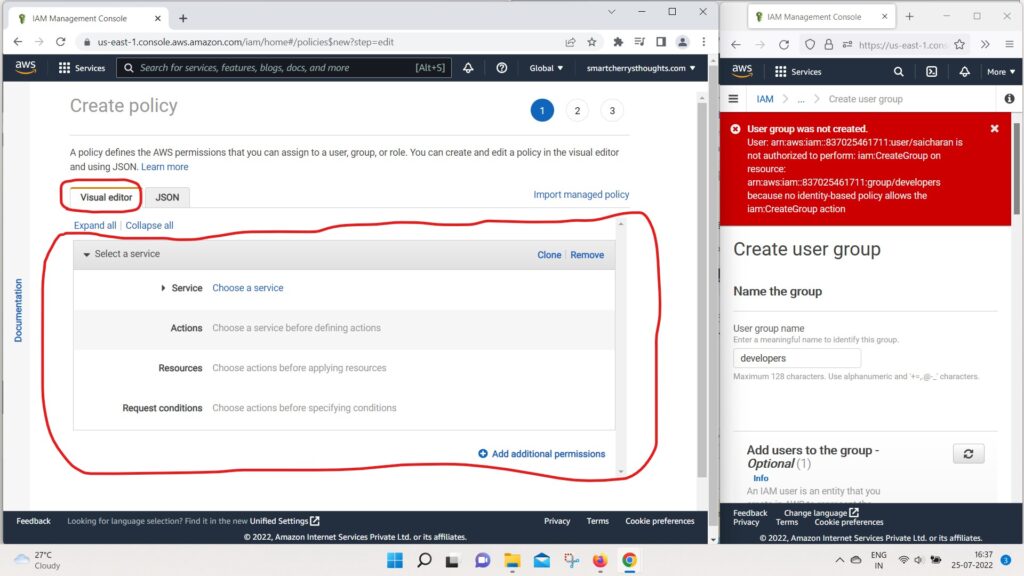
- For Example, we can choose the service IAM,
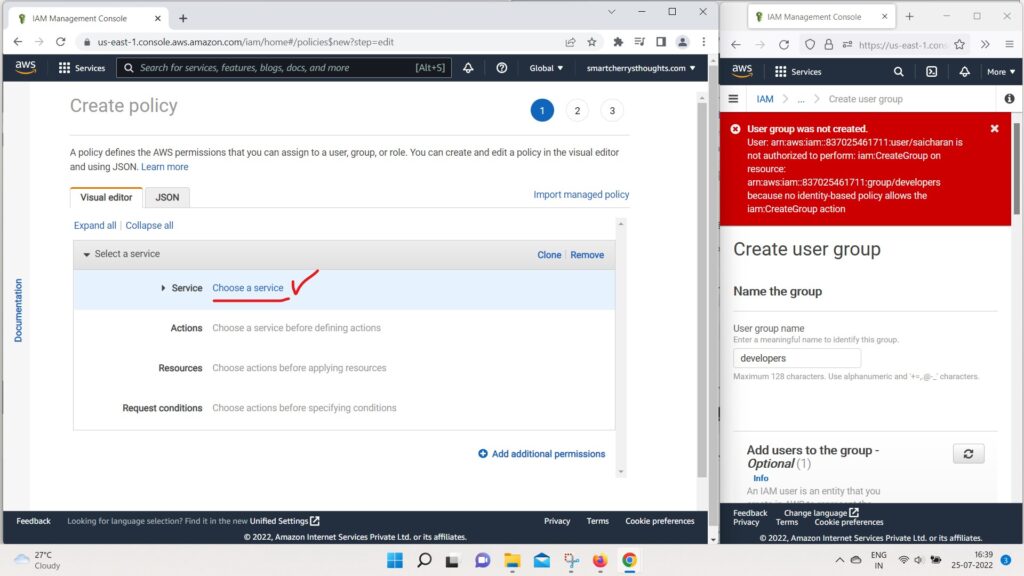
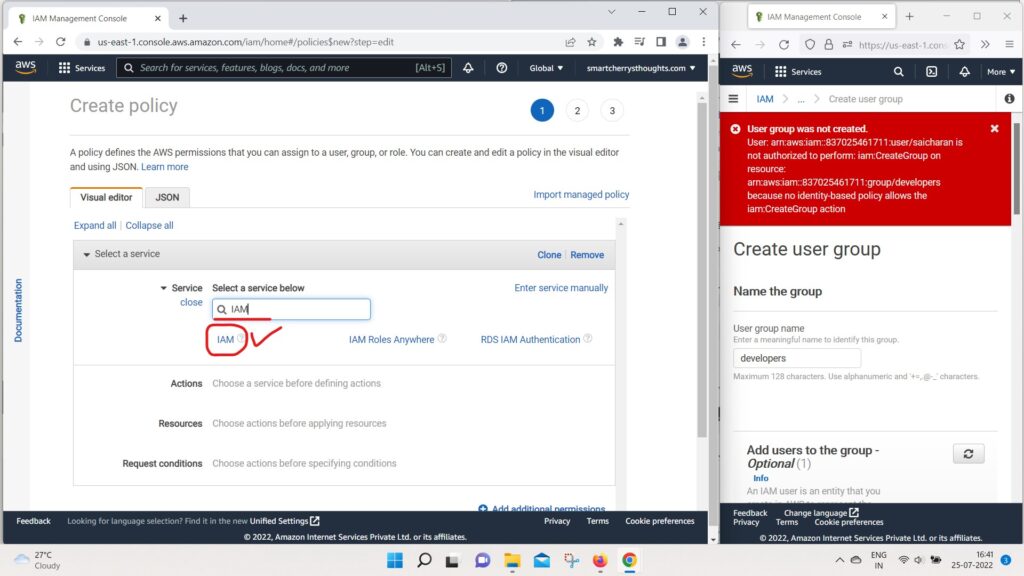
- then we can choose an Action.
- And we can, for example, do a ListUser,
- so I Can filter for list users
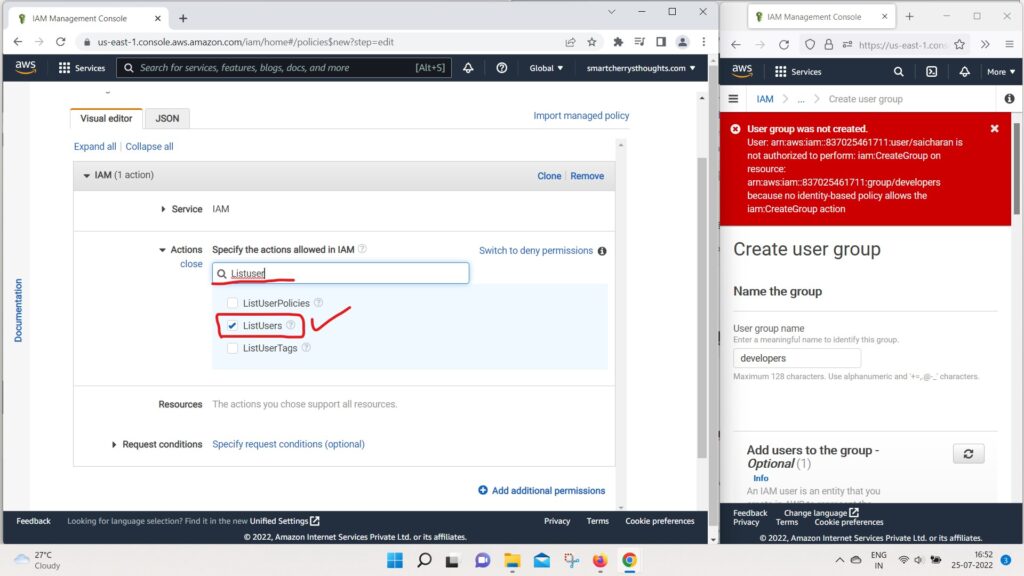
- for Effects and I can do GetUser.
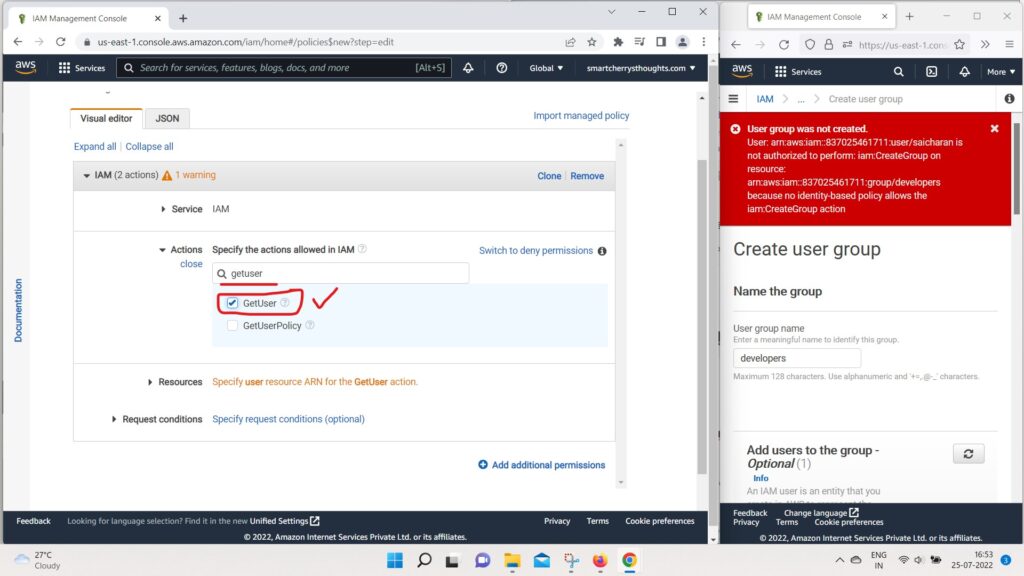
- So let’s say we want to add these two actions
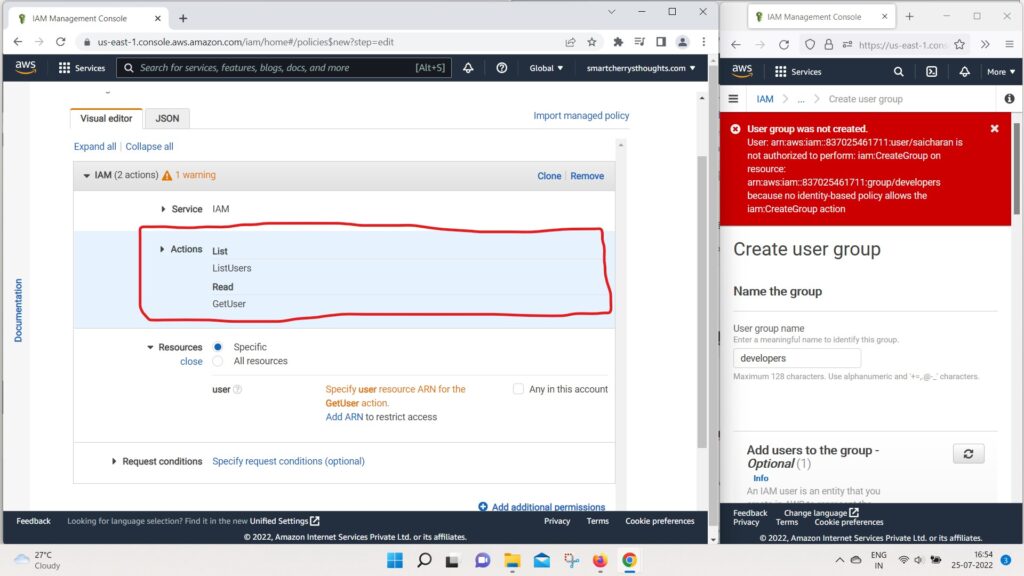
- and on the Resources we can specify specific resources.
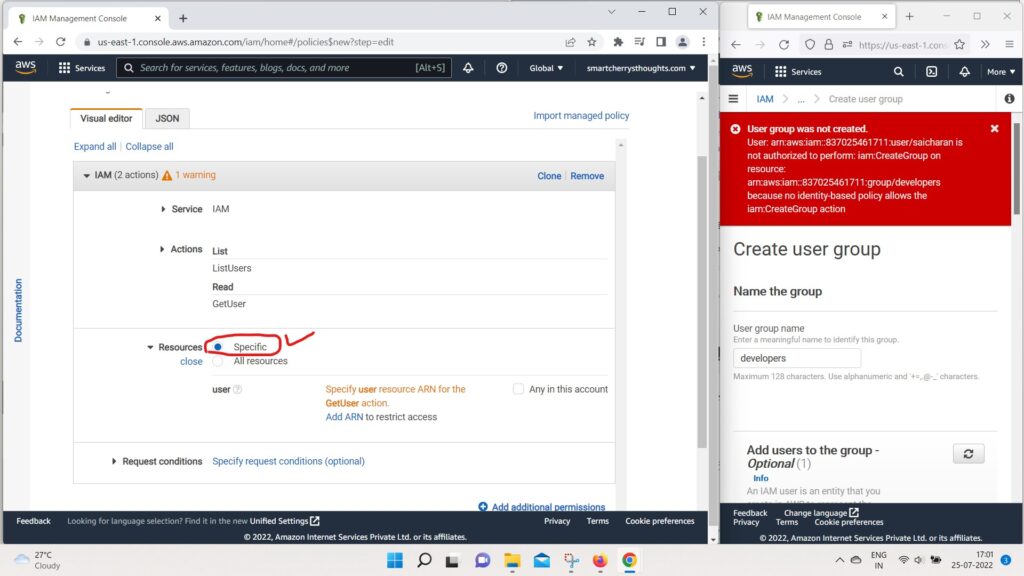
- or all resources.
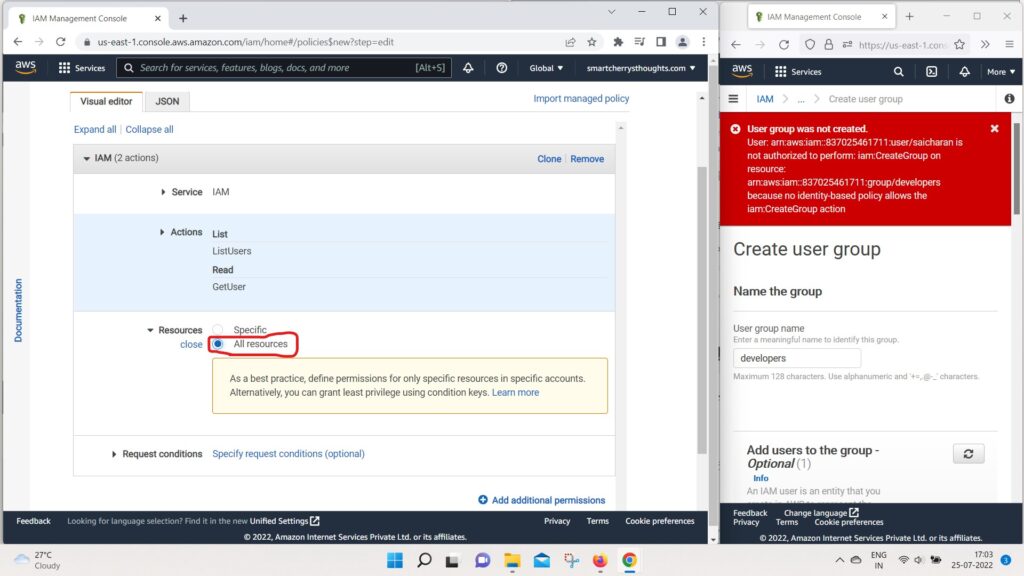
- we could also specify a request condition if we wanted to.
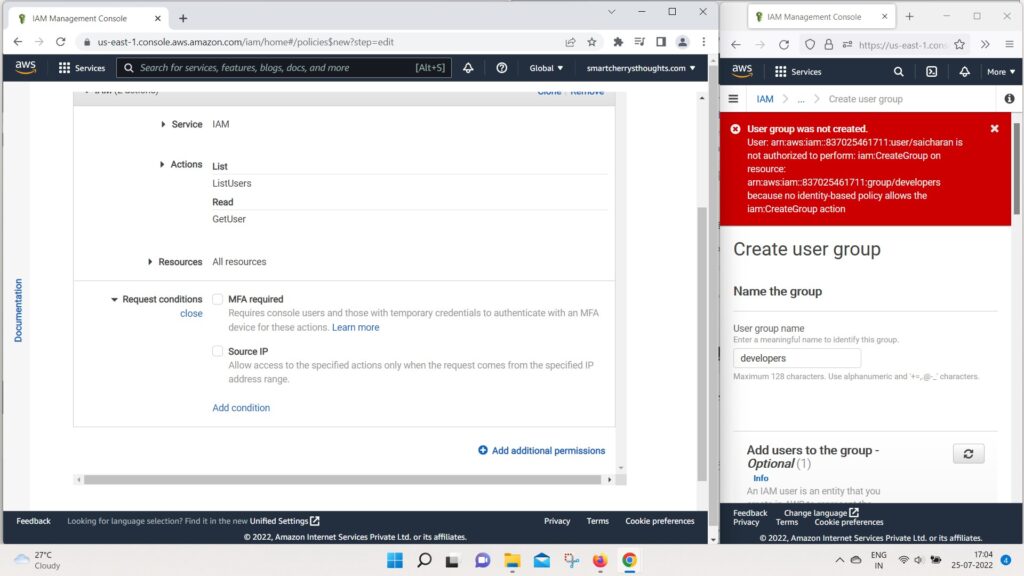
- So, once we’ve done that
- if we go to the JSON documents
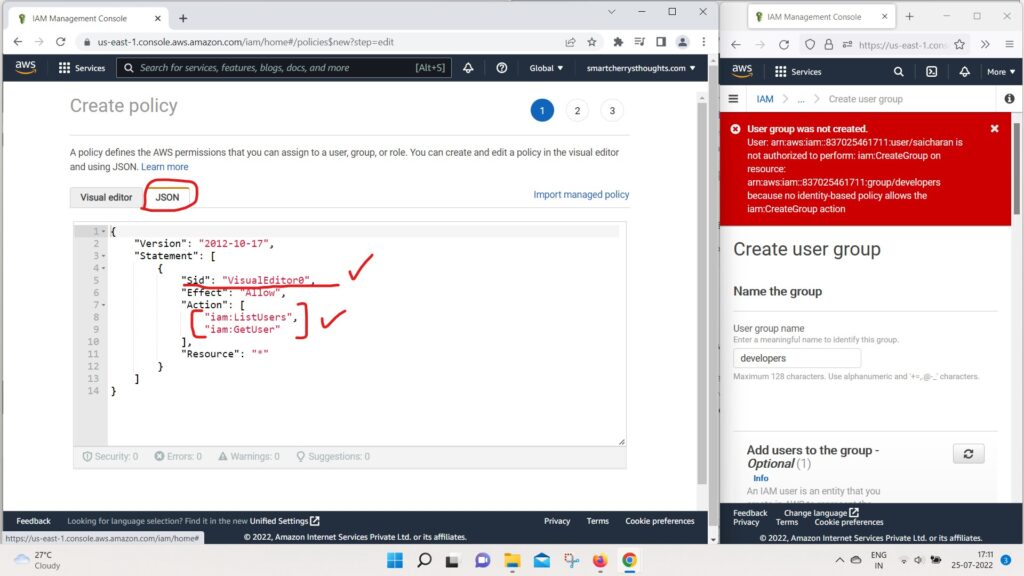
- as we can see the visual editor SID was Added,
- which has the statement ID,
- and we have two actions that were added.
- So IAM list users and get users on resource start.
- So it’s quite a handy way to generate JSON directly
- from the visual editor.
- Okay, So just to finish this lecture,
- let’s do a few things.
- In user groups, I’m going to delete the developers group
- cause i dont need it.
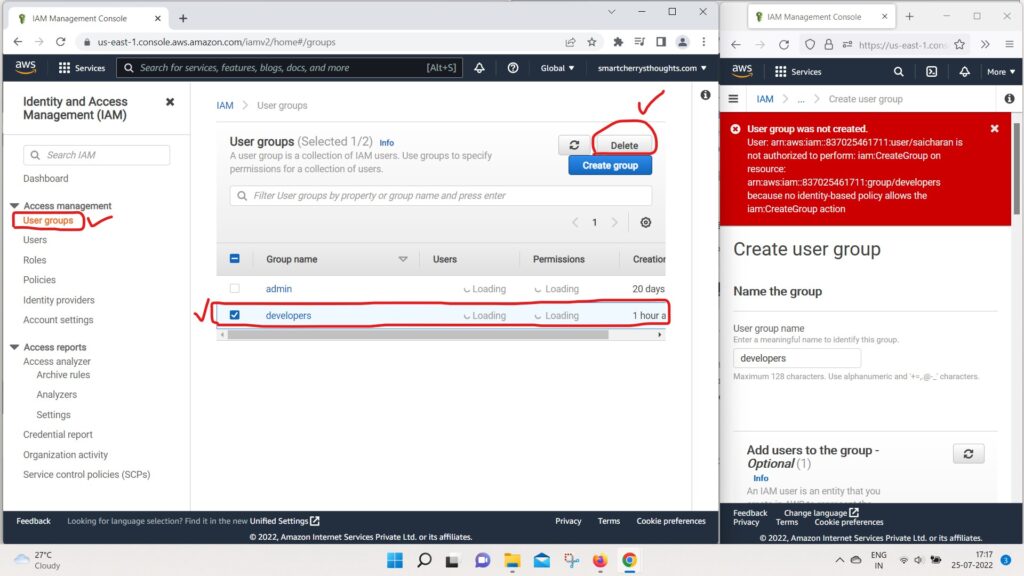
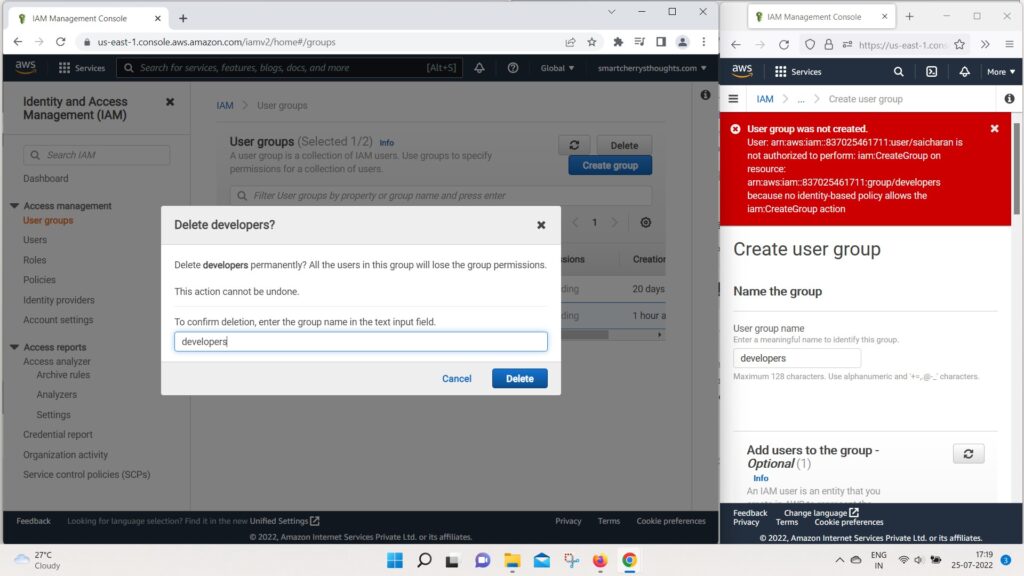
- and i need you to type the name of the group,
- so i will type developers and click on delete.
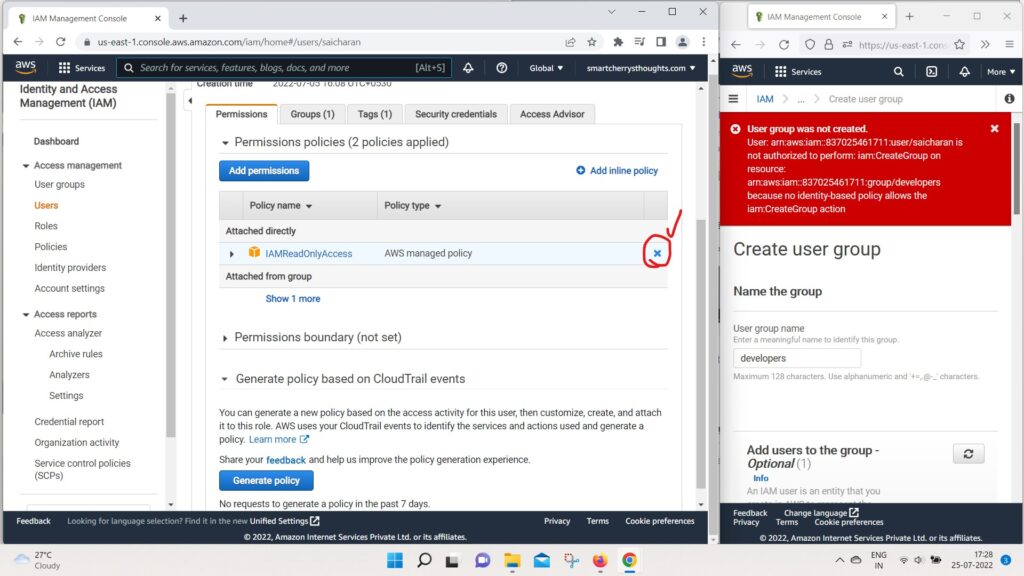
- And also on my Users as saicharan,
- I’m going to remove the policy that was attached directly.
- because we dont need this IAM read onlyAcess policy.
- I will just remove it and we’re good to go.
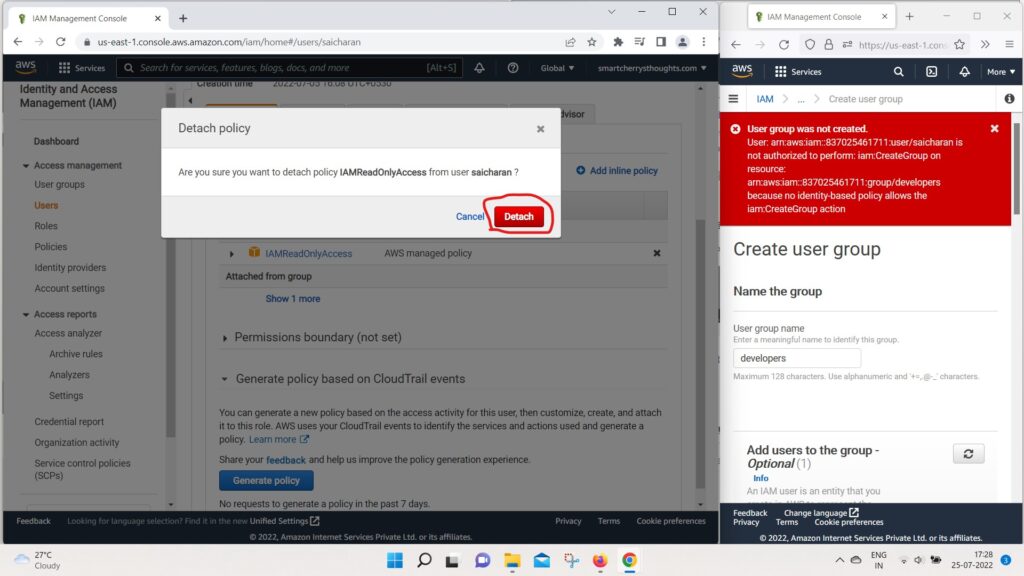
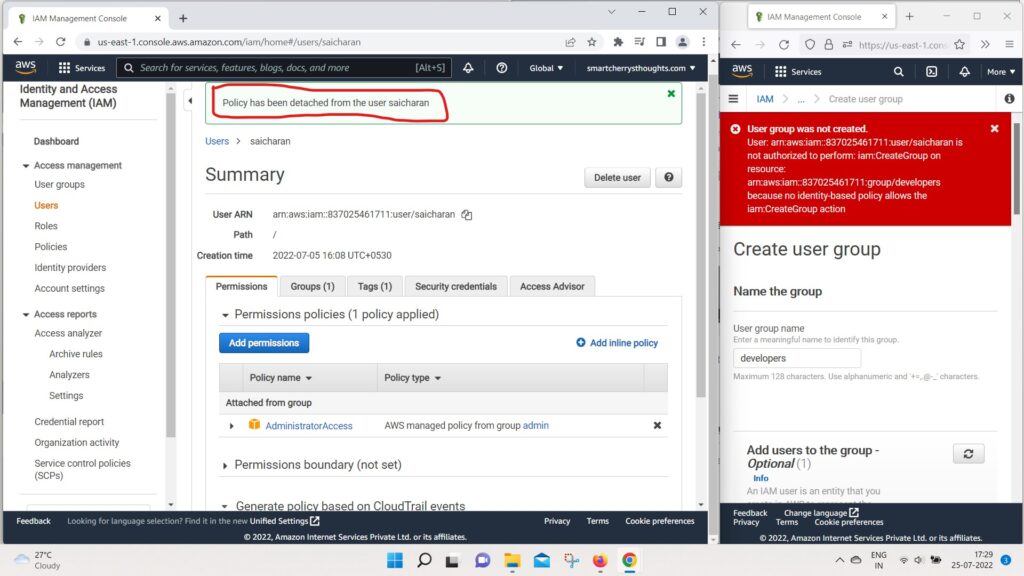
- So, now my user saicharan has a full administrator access
- because it is inherited from the admin group.
- And so obviously if I go back to my IAM also on the right side.
- as we can see, everything is working just fine.
- So I will just refresh and here we go.
- thing are working.
- So that’s it for this lecture.
- I hope you liked it.
- and i will see you in the next lecture.


Thank you for your shening. I am worried that I lack creative ideas. It is your enticle that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.com/en/register?ref=P9L9FQKY
The point of view of your article has taught me a lot, and I already know how to improve the paper on gate.oi, thank you. https://www.gate.io/fr/signup/XwNAU
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://www.binance.com/join?ref=53551167