5) IAM MFA Overview(IAM Password Policy)- AWS Certified Solutions Architect Associate Course SAA-C02- Now that we have created users and groups, it is time for us to protect these users and groups from being compromised.
- So for this we have two defense mechanisms.
- The first one is to define what’s called a Password Policy.
- Why?
- Well’ because the stronger the password you use
- the more security for your accounts.
- So in AWS, you can set up a password policy.
- with different options.
- The first one is you can set a minimum password length.
- and you can require specific character types,
- for example, you may want to have an uppercase letter,
- lowercase letter, number, non-alphanumeric characters,
- for example a questions mark and so on.
- Then you can allow or not,
- IAM users to change their own passwords
- or you can require users to change their password.,
- after some time, to make your password expired,
- for example, to say every 90 days, users have to change their passwords.
- Finally, you can also prevent password reuse.
- so that users when they change their passwords,
- dont change it to the one they already have
- or change it to the one they had before.
- So this is great, a password policy, really is helpful,
- against brute force attacks on your accounts.
- But there’s a second defense mechanism.
- that you need to know, going into the exam,
Multi Factor Authentication- MFA
- and this is the Multi Factor Authentication or MFA.
- It is possible you already to use it, on some websites.
- but on AWS it’s a must and it’s very recommended to use it.
- So, users have access to your account,
- and they can possibly do a lot of things,
- especially if they’re, administrators,
- they can change configuration, delete resources.
- and other things.
- So you absolutely want to protect at least
- your Root Accounts and hopefully all your IAM users.
- so how do you protect them on top of the password?
- Well, you use an MFA device.
- So what is MFA?
- MFA is using the combination of a password that you know,
- and a security device that you own.
- and these two things together,
- have a much greater security than just a password.
- So for example, let us take Alice.
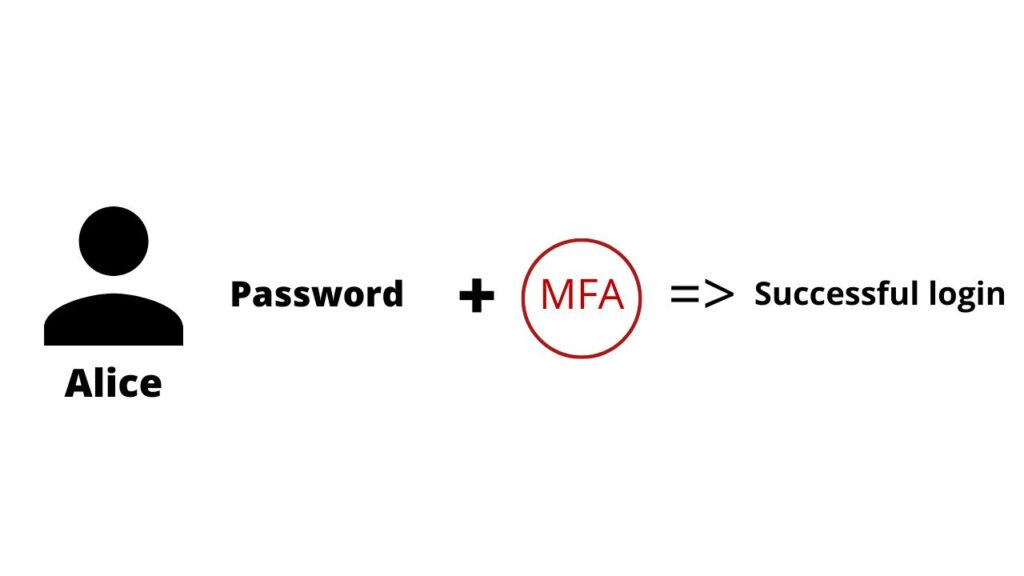
- Alice Knows her password,
- but she also has an MFA Generating token.
- and by using these things together while logging in,
- she is going to be able to do a successful login on MFA.
- so the benefit of MFA is that even if Alice
- has lost her password, because it’s stolen or it’s hacked,
- the account will not be compromised because the hacker,
- will need to also get a hold of the physical device.
- of Alice that could be a phone for example to do a login.
MFA Devices Options in AWS
- Obviously, that is much less likely.
- So what are the MFA devices option in AWS
- and you should know them going to the exam.
- but don’t worry they’re quite simple.
- The first one is a Virtual MFA device,
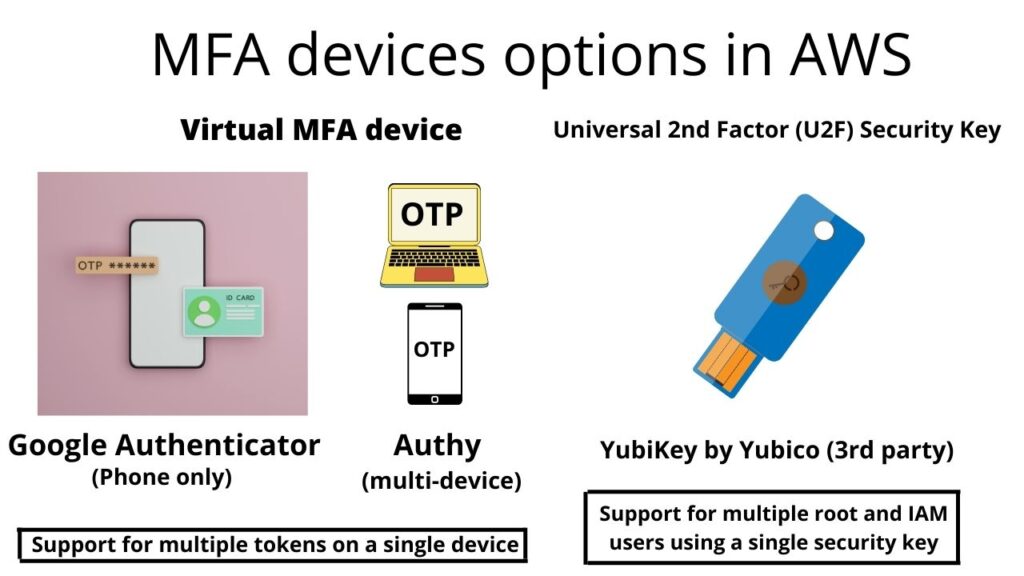
- this is what we’ll be using in the hands on
- and so you can use Google Authenticator,
- which is just working on one phone at a time,
- or using Authy which is multi-device
- They both work the same except one is multi-device.
- And personally I use Authy because I like the fact that
- I can use it on my computer and on my phones.

- So, for Authy you have support
- for multiple tokens on a single device.
- So, that means that with a Virtual MFA device,
- you can have your root account, your IAM user,
- and another account, and another IAM user,
- its up to you, you can have as many users
- and accounts as you want on your Virtual MFA device,
- which make it a very easy solution to use.

- Now we have another thing called
- a universal 2nd Factor or U2F Security Key,
- and that is a physical device, for example,
- a YubiKey by Yubico and Yubico is a a 3rd party to AWS,
- this is not the AWS that provided, this is a 3rd party
- and we use a physical device,
- because maybe it’s super easy, you put it your Key fobs
- and you’re good to go.
- So this YubiKey supports multiple root and IAM users
- using a single security so you don’t need as many keys
- as users otherwise that will be a nightmare.
- Then your other options,

- you have a hardware key Fob MFA device
- for example this one provided by Gemalto
- which is also a third party to AWS
- and finally, if you are using the cloud of the government.

- in the US, The AWS GovCloud then you have a special Key Fob,
- That looks like this, that is provided by SurePassID
- which is also a 3rd party.
- So that’s it, we’ve seen the theory
- on how to protect your account.
- but let’s go the next lecture to implement that.
- So I will see you in the next lecture.

I may need your help. I tried many ways but couldn’t solve it, but after reading your article, I think you have a way to help me. I’m looking forward for your reply. Thanks.
Yet, there’s more. The heart of any prosperous listings platform lies in its convenience of application. Interestingly, this From Russia treasure embraces an intuitive posting process that guarantees even beginner users can quickly post their products. From uploading pictures to providing brief summaries, the process is streamlined to preserve time and minimize barriers.
It’s amazing in favor of me to have a site, which is useful
in support of my knowledge. thanks admin
powered by GoToTop.ee
https://ru.gototop.ee/
One thing I would really like to say is the fact car insurance cancellation is a horrible experience and if you are doing the proper things like a driver you simply will not get one. A number of people do receive the notice that they’ve been officially dumped by their insurance company and several have to scramble to get added insurance after having a cancellation. Inexpensive auto insurance rates are often hard to get from cancellation. Having the main reasons with regard to auto insurance termination can help drivers prevent sacrificing one of the most important privileges readily available. Thanks for the tips shared by means of your blog.
Excellent way of telling, and fastidious article to take information about
my presentation subject matter, which i am going to convey in institution of higher education.
powered by GoToTop.ee
https://ru.gototop.ee/
Wie profitiere ich von SmartBCH / DeFi? https://bchpls.org/wie-profitiere-ich-von-smartbch-defi/
I am curious to find out what blog system you
are utilizing? I’m having some small security issues with my latest site and I would like to find something
more safe. Do you have any solutions?
powered by GoToTop.ee
https://ru.gototop.ee/
Great post. I used to be checking continuously this weblog and I’m impressed!
Extremely useful information specifically the final section :
) I handle such information a lot. I used to be looking for this
particular information for a long time. Thank you and best
of luck.
powered by GoToTop.ee
https://ru.gototop.ee/
Fantastic article! The information you provide is important. Thank you for sharing!
Excellent beat ! I wish to apprentice whilst you amend your website,
how can i subscribe for a blog website? The
account aided me a appropriate deal. I were a little bit acquainted
of this your broadcast provided vibrant transparent concept
powered by GoToTop.ee
https://ru.gototop.ee/
I visited several blogs but the audio quality for audio songs existing at this web site is in fact marvelous.
I appreciate the effort and time you’ve spent in putting together this information. Thank you for sharing this with us.
You’ve got a great thought
https://resources.spicetokens.com
Keep this going please, great job!
Thank you for your help and this post. It’s been great.
Do you mind if I quote a few of your articles
as long as I provide credit and sources back to your website?
My blog is in the very same area of interest as yours and my visitors would genuinely benefit
from some of the information you present here. Please
let me know if this okay with you. Cheers!
You need to be a part of a contest for one of the finest websites on the net.
I am going to highly recommend this web site!
I love how you’ve broken down complex ideas into simple, understandable concepts. Watch War Movies Online
Using Electron Cash over I2P network – https://wiki.electroncash.de/wiki/Using_Electron_Cash_over_I2P
https://wiki.electroncash.de/wiki/Imaginary.cash Imaginary.cash
On the iOS system, you have to set up an app called Documents.
You can both choose to visit the official web site
or simply add ‘ss’ to the video URL to launch the video downloading course
of.
Мне понравилась систематическая структура статьи, которая позволяет читателю легко следовать логике изложения.
Статья содержит обширную информацию и аргументы, подтвержденные ссылками на достоверные источники.
Читателям предоставляется возможность самостоятельно исследовать представленные факты и принять собственное мнение.
Wow, this paragraph is fastidious, my younger sister is analyzing these kinds of things, therefore I am going to let know her.
Freak Doll, Nasty Ricky, Rick Nasty Only Fans Leaks Mega Folder( https://Discord.GG/UCS )
Princess Emily, Annabel Redd, The Hemp Honey Only Fans Leaks Mega Folder Link( https://UrbanCrocSpot.org/ )
Мне понравилось объективное представление разных точек зрения на проблему.
Hello, everything is going sound here and ofcourse every one is sharing information, that’s in fact excellent, keep up writing.
Статья содержит актуальную информацию, которая помогает понять сложность и важность проблемы.
Great tips Regards.
Your article helped me a lot, is there any more related content? Thanks! https://www.binance.com/de-CH/register?ref=V2H9AFPY
You can select whether you want to reserve it as MP4
or MP4 HD.
Thank you for writing this post!
The articles you write help me a lot and I like the topic
May I have information on the topic of your article?
Мне понравилась четкая и логическая структура статьи, которая облегчает чтение.
Great beat ! I would like to apprentice while you amend your web site, how could i subscribe for a blog site? The account helped me a acceptable deal. I had been a little bit acquainted of this your broadcast provided bright clear concept
Я нашел в статье несколько интересных фактов, о которых раньше не знал.
Thank you for being of assistance to me. I really loved this article.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://accounts.binance.com/uk-UA/register?ref=V3MG69RO
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://accounts.binance.com/de-CH/register-person?ref=53551167
Эта статья является настоящим источником вдохновения и мотивации. Она не только предоставляет информацию, но и стимулирует к дальнейшему изучению темы. Большое спасибо автору за его старания в создании такого мотивирующего контента!
Автор статьи представляет разнообразные факты и статистику, оставляя решение оценки информации читателям. Это сообщение отправлено с сайта https://ru.gototop.ee/
Стиль написания в статье ясный и легко читаемый.
Your article helped me a lot, is there any more related content? Thanks! https://accounts.binance.com/ka-GE/register?ref=53551167
I have been surfing online more than 2 hours today, yet
I never found any interesting article like yours. It is pretty worth enough for me.
Personally, if all website owners and bloggers made good content as you did, the net will
be a lot more useful than ever before.
I think the admin of this web site is really working hard in support of his site, since here every data is quality based data.
Very rapidly this site will be famous among all blog viewers, due to it’s good content
Thanks for the recommendations you have contributed here. Yet another thing I would like to say is that laptop memory demands generally go up along with other developments in the technologies. For instance, any time new generations of cpus are brought to the market, there is usually a corresponding increase in the scale demands of both the personal computer memory along with hard drive room. This is because software program operated by means of these cpus will inevitably surge in power to take advantage of the new technology.
I don抰 even know how I ended up here, but I thought this post was great. I do not know who you are but certainly you’re going to a famous blogger if you are not already 😉 Cheers!
Nice weblog right here! Additionally your site lots up very fast! What host are you the usage of? Can I am getting your affiliate hyperlink to your host? I desire my website loaded up as fast as yours lol
Thanks for sharing your ideas. I might also like to say that video games have been ever evolving. Modern technology and innovative developments have made it simpler to create realistic and enjoyable games. These types of entertainment video games were not as sensible when the real concept was first of all being tried out. Just like other styles of electronics, video games too have had to develop by way of many generations. This itself is testimony to the fast development of video games.
Good post made here. One thing I would like to say is the fact most professional career fields consider the Bachelors Degree like thejust like the entry level requirement for an online degree. While Associate Certification are a great way to get started, completing your current Bachelors presents you with many good opportunities to various professions, there are numerous internet Bachelor Course Programs available by institutions like The University of Phoenix, Intercontinental University Online and Kaplan. Another thing is that many brick and mortar institutions present Online variants of their certifications but commonly for a considerably higher charge than the firms that specialize in online college diploma plans.
These days of austerity in addition to relative panic about getting debt, many people balk contrary to the idea of having a credit card to make purchase of merchandise or pay for any gift giving occasion, preferring, instead to rely on the actual tried plus trusted approach to making repayment – cash. However, if you’ve got the cash on hand to make the purchase completely, then, paradoxically, this is the best time for you to use the credit card for several factors.
Статья содержит информацию, которая актуальна для современного общества и его вызовов.
Мы предлагаем сделать «ссылочный прогон» для вашего сайта.
О нас: Мы являемся компанией, более 10-ти лет предоставляющей
услуги «ссылочного прогона»
(массового размещения ссылок на сторонних сайтах) и хотели бы предложить вам данную
услугу. В результате, через 3-5 дней, DR (Domain Rating) рейтинг вашего
домена повысится, что положительно отразится на
выдаче вашего сайта в Гугле и Яндексе.
Если размещать ссылки на регулярной основе, то через 1-3 месяца,
также, повысится и Яндекс показатель ИКС сайта.
На сегодняшний день, это самый быстрый
и недорогой вариант повышения авторитета сайта и улучшения его позиций
в выдаче. Стоимость прогона составляет от 2 000 руб.
и выше (и зависит от объёма размещаемых ссылок).
Подробности см. на нашем сайте https://gototop.ee/ или пишите
мне на alexey@gototop.ee Спасибо